Dev Tools: Difference between revisions
m (→fail0VERFLOW) |
(Add SPRXPatcher) |
||
| (128 intermediate revisions by 24 users not shown) | |||
| Line 1: | Line 1: | ||
== Tools == | |||
==Tools== | |||
[http://pastie.org/1430104 hexkey2bin.c] | [http://pastie.org/1430104 hexkey2bin.c] | ||
| Line 14: | Line 13: | ||
[http://pastie.org/private/vgrajylkeetkem7ommqdta downgrade] | [http://pastie.org/private/vgrajylkeetkem7ommqdta downgrade] | ||
==Git== | == Git == | ||
[http://library.edgecase.com/git_immersion/ git docs] | [http://library.edgecase.com/git_immersion/ git docs] | ||
== SceTool == | |||
* [http://www.psdevwiki.com/files/devtools/scetool/ scetool] / [http://www.sendspace.com/file/a0an56] (Windows) | |||
** [http://mir.cr/MLZONDKY cygwin-dll.rar] (needed in case of cygwin1.dll missing error) | |||
* <!--// https://www.dropbox.com/sh/9tp1x59jd5z34qa/10BT-4IDxX //-->[https://www.dropbox.com/sh/9tp1x59jd5z34qa/QBcYdjPA9q/ps3/release/scetool_0.2.9.7z scetool_0.2.9.7z] (Linux) | |||
* [http://www.2shared.com/file/Lshbj21H/scetool_029_mac.html scetool_0.2.9] (OSX) | |||
<s>common for all above: [http://pastie.org/8026816 keys]</s> | |||
scetool 0.2.7 <public build> (C) 2011-2012 by naehrwert | |||
NP local license handling (C) 2012 by flatz | |||
=== Setup === | |||
- /data/keys : Keyfile. | |||
- /data/ldr_curves : Loader curves (7744 bytes). | |||
- /data/vsh_curves : VSH curves (360 bytes). | |||
- /data/idps : IDPS as binary file | |||
- /data/act.dat : act.dat | |||
- /rifs/* : *.rif files | |||
- /raps/* : *.rap files | |||
==== Keyfile format ==== | |||
[keyname] | |||
type={SELF, RVK, PKG, SPP, OTHER} | |||
revision={00, ..., 18, 8000} | |||
version={..., 0001000000000000, ...} | |||
self_type={LV0, LV1, LV2, APP, ISO, LDR, UNK_7, NPDRM} | |||
key=... | |||
erk=... | |||
riv=... | |||
pub=... | |||
priv=... | |||
ctype=... | |||
====Keyset example==== | |||
[metldr] | |||
type=SELF | |||
revision=00 | |||
self_type=LDR | |||
erk=0000000000000000000000000000000000000000000000000000000000000000 | |||
riv=00000000000000000000000000000000 | |||
pub=00000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
priv=000000000000000000000000000000000000000000 | |||
ctype=00 | |||
====NPDRM key(set) names==== | |||
- [NP_tid]: Title ID OMAC1 key. | |||
- [NP_ci]: Control info OMAC1 key. | |||
- [NP_klic_free]: Free klicensee. | |||
- [NP_klic_key]: klicensee key. | |||
- [NP_idps_const]: IDPS constant. | |||
- [NP_rif_key]: rif key. | |||
- [NP_sig]: Footer signature ECDSA keyset. | |||
==== Error: Could not find keyset for SELF ==== | |||
Unlike unself, scetool does not bruteforce keys. So if you are trying to decrypt a file that is using a 4.75 key (4.20-{{latestPS3}}) and you only have that same key under : | |||
4.20 {{dot}} 4.21 {{dot}} 4.22 {{dot}} 4.23 {{dot}} 4.25 {{dot}} 4.26 {{dot}} 4.30 {{dot}} 4.31 {{dot}} 4.40 {{dot}} 4.41 {{dot}} 4.45 {{dot}} 4.46 {{dot}} 4.50 {{dot}} 4.55 {{dot}} 4.60 {{dot}} 4.65 {{dot}} 4.66 {{dot}} 4.70 | |||
it will error out. | |||
To see which key version is used by that complaining SELF, use: | |||
<code>scetool -i file_in</code> | |||
and add the missing key(s) | |||
if that produces a line like: | |||
<code>Key Revision [DEBUG]</code> | |||
the file is an fself (debug == no keys), just strip the first 0x90 bytes and save | |||
===Help text=== | |||
USAGE: scetool [options] command | |||
==== Commands ==== | |||
COMMANDS Parameters Explanation | |||
-h, --help Print this help. | |||
-k, --print-keys List keys. | |||
-i, --print-infos file_in Print SCE file info. | |||
-d, --decrypt file_in file_out Decrypt/dump SCE file. | |||
-e, --encrypt file_in file_out Encrypt/create SCE file. | |||
==== Options ==== | |||
OPTIONS Possible Values Explanation | |||
-v, --verbose Enable verbose output. | |||
-r, --raw Enable raw value output. | |||
-0, --sce-type SELF/RVK/PKG/SPP [[SCE File Types|SCE File Type]] | |||
-1, --compress-data TRUE/FALSE(default) Whether to compress data or not. | |||
-s, --skip-sections TRUE(default)/FALSE Whether to skip sections or not. | |||
-2, --key-revision e.g. 00,01,...,0A,... [[Revision versus Version|Key Revision]] | |||
-m, --meta-info Use provided meta info to decrypt. | |||
-3, --self-auth-id e.g. 1010000001000003 [[Program Authority ID]] | |||
-4, --self-vendor-id e.g. 01000002 [[Program Vender ID]] | |||
-5, --self-type LV0/LV1/LV2/APP/ISO/ | |||
LDR/NPDRM [[Program Type]] | |||
-6, --self-fw-version e.g. 0003004100000000 [[Revision versus Version|Firmware Version]] | |||
-7, --self-add-shdrs TRUE(default)/FALSE Whether to add ELF shdrs or not. | |||
-8, --self-ctrl-flags 32 bytes Override [[Control Flags|control flags]]. | |||
-9, --self-cap-flags 32 bytes Override [[Capability Flags|capability flags]]. | |||
-b, --np-license-type LOCAL/FREE [[License Types|License Type]] | |||
-c, --np-app-type SPRX/EXEC/UPDATE [[App Types|App Type]] | |||
-f, --np-content-id Content ID | |||
-l, --np-klicensee 16 bytes Override klicensee. | |||
-g, --np-real-fname e.g. EBOOT.BIN Real Filename | |||
-j, --np-add-sig TRUE/FALSE(default) Whether to add a NP sig. or not. | |||
=== History === | |||
==== Version 0.2.7 ==== | |||
- Added local NP license handling. | |||
- Added option to override klicensee. | |||
- Added option to disable section skipping (in SELF generation). | |||
==== Version 0.2.5 ==== | |||
- Added option to use provided metadata info for decryption. | |||
- "PS3" path environment variable will now be searched for keys/ldr_curves/vsh_curves too. | |||
==== Version 0.2.4 ==== | |||
- Added option to display raw values. | |||
- Moved factory Auth-IDs to <public build> (as they are on psdevwiki now). | |||
==== Version 0.2.2 ==== | |||
- Added options to override control/capability flags (32 bytes each). | |||
- Fixed where a false keyset would crash scetool when decrypting a file. | |||
- Some source level changes and optimizations. | |||
==== Version 0.2.1 ==== | |||
- [http://www.psdevwiki.com/files/devtools/scetool/zlib1.dll zlib] [http://mir.cr/1PQW9REH] is required to use scetool. | |||
- 'sdk_type' was changed to 'revision' in data/keys. | |||
== OpenSCETool == | |||
https://github.com/spacemanspiff/oscetool | |||
== Break N Make (MakeSelf & BreakSelf) == | |||
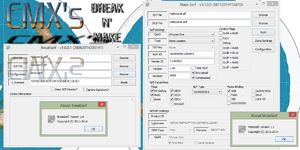
[[File:Make Self v1.1.0.0 (08112014153810).png|300px|Make Self v1.1.0.0 (08112014153810)]] | |||
=== Download === | |||
'''Download:''' https://www.mediafire.com/?f9aaj86vn0w4nn1 [https://mega.co.nz/#!2oVC3BJD!hNEbAHyO6H8Mug0ipoonlA5V2Mzosd0QrB6E-xTMc8Y mirror] | |||
=== Key.conf === | |||
http://pastie.org/9821745 <- dead link | |||
=== Features === | |||
* Win32 GUI Version | |||
* Drag and Drop of bin.self.SPRX (Will Open if Klic Key needs changing) | |||
* Changing of Decyption Klic | |||
* Decryption of NPDRM | |||
* Uses Key.conf to add new Keys if necessary (iso/app/npdrm/lv0/lv1/lv2 keys) | |||
* Can be added (Manually) to Right click Function for Quick Decryption | |||
=== Changelog === | |||
==== V1.1 (08-11-2014) ==== | |||
* Added Control Flags 0x1B = 0x10 | |||
* Changed Wording For Flag "default licensee" to First Boot.. | |||
* Moved Configuration Section into its own Button | |||
** Now you can set the Configuration for the ini files inside | |||
* Added in klicensee.ini | |||
** This allows you to Database your own Personal Keys. | |||
* Added ability to Change DRM Type | |||
** Checks for it in the klicensee.ini will set new key if pressent | |||
* Added Quick Selector | |||
** (Reads from klicensee.ini) in NPDRM Settings Area for any preprogramed files.. | |||
* Added Drag and Drop to Clone | |||
** (Can now Drop file you want to use for Clone "ANY" place outside of the Elf/Self File Sections and it will read it to try and clone it) | |||
* Upgraded Clone Function (this will use klicensee.ini) | |||
** If the file is present inside the klicensee.ini it will auto detect when you Clone the original file. | |||
===== New Klicensee.ini what is it? ===== | |||
First Format | |||
[klicensee] | |||
title= | |||
productid= | |||
filename= | |||
flags= | |||
key0= | |||
key1= | |||
key2= | |||
key3= | |||
key4= | |||
[/klicensee] | |||
Explaination | |||
* title = | |||
is the title you will see in Quick Selection area. (Put what you would like) | |||
* productionid = | |||
this is the 36character ID that belongs to the game (eg: UP1017-BLUS30682_00-GTACOMPLETEV0102) | |||
* filename = | |||
the name to the file this works for so Eboot/SPRX/SELF and so on) (note 1 name per [klicensee] section) | |||
* flags = | |||
20 Game Update / 01 First boot
. Note that they Stack so 21 both on | |||
* Key0= | |||
Disc (normaly just normal Free key no need to put) | |||
* Key1= | |||
Network (Normaly the same as RiF key) | |||
* Key2= | |||
Local (This is your Personal Rif key) | |||
* Key3= | |||
Free (for Eboots this key is the normal Free key, for Sprx,Selfs this key can be found inside the Eboot to decypt the Sprx,Self) | |||
* Key4= | |||
for PSP | |||
Note : you only need to put the Key section you plan to use. | |||
here is an example setup | |||
[klicensee] | |||
title=GTACOMPLETE SELF | |||
productid=UP1017-BLUS30682_00-GTACOMPLETEV0102 | |||
filename=GTAIV.self | |||
key3= 00000000000000000000000000000000 | |||
[/klicensee] | |||
==== V1.0 - Original (29-10-2011) ==== | |||
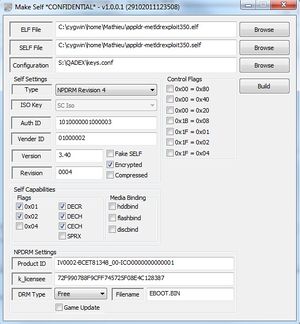
[[File:Make Self v1.0.0.1 (29102011123508).jpg|300px]] | |||
* Allows you to Encrypt (Dex)+(CEX)+(NPDRM) Bin,Self,Sprx,Isoself | |||
* Has Clone Function | |||
* Allows for Multi control over how files are encrypted .. | |||
* Allows for Setup of Quick Settings inside Quick.ini | |||
* Updatable keys.conf uses same one as Breakself. | |||
* Allows for Encrypting Using original | |||
===== What is Clone? ===== | |||
* Clone Settings from Original Encrypted file | |||
Press Clone Settings then pick original Encrypted file .. If NPDRM you may need to fill in the K_Licensee with decrypt key Before doing the Clone.. | |||
== NPDTool v4d == | |||
*http://mir.cr/1VI625HY | |||
*http://mir.cr/NUUBDXDI | |||
npdtool v4d by '''belmondo''' and '''user''' ©2014 | |||
usage decrypt: npdtool [mode] infile outfile [rap/idps/klic] [act] [rif] | |||
[mode]: d (decrypt edata using idps, act.dat and rif) | |||
dk (decrypt edata using k_licensee) | |||
dr (decrypt edata using rap) | |||
ds (decrypt sdata) | |||
usage encrypt edata: npdtool [format] infile outfile [klic] [cID] [block] | |||
[format]: 1 (format1 edata) | |||
1c (format1 compressed edata) | |||
2 (format2 edata) | |||
2c (format2 compressed edata) | |||
3 (format3 edata) | |||
3c (format3 compressed edata) | |||
4 (format4 edata) | |||
4c (format4 compressed edata) | |||
[cID]: XX0000-YYYY00000_00-0000000000000000 | |||
[block]: not for compressed [MAX 8000] | |||
usage encrypt goma: npdtool [format] [cID] | |||
[format]: goma (licence edata) | |||
[cID]: XX0000-YYYY00000_00-0000000000000000 | |||
usage encrypt sdata: npdtool [format] infile outfile [block] | |||
[format]: 1s (format1 sdata) | |||
2s (format2 sdata) | |||
2sc (format2 compressed sdata) | |||
3s (format3 sdata) | |||
3sc (format3 compressed sdata) | |||
4s (format4 sdata) | |||
4sc (format4 compressed sdata) | |||
[block]: not for compressed [MAX 8000] | |||
usage bruteforce: npdtool [mode] inNPD inELF outK_lic.bin | |||
[mode]: b (bruteforce k_licensee in hex) | |||
b2 (bruteforce k_licensee in ascii) | |||
usage info: npdtool [mode] inNPD | |||
[mode]: i (info) | |||
== PSNope == | |||
by u$er - latest version 1.06? | |||
== PSN Patch == | |||
(psidpatch+psnope) | |||
*http://store.brewology.com/ahomebrew.php?brewid=244 v4.70.06 by KW | |||
==SDATA Tool== | |||
Small open source tool to unpack and decrypt SDATA files. All the hard work and reverse engineering done by Hykem, along with collaboration of AlexAltea and BlackDaemon. It supports all SDATA file variants: v1 to v4, compresed or uncompressed, debug or release SDATAs. | |||
Link: <!-- Old: https://github.com/AlexAltea/sdata-tool --> https://github.com/inaina/sdata-tool | |||
Usage: ''sdata-tool.exe <input> <output>'' | |||
==fail0VERFLOW== | ==fail0VERFLOW== | ||
| Line 69: | Line 346: | ||
:unself_gnpdrm | :unself_gnpdrm | ||
::usage: unself_gnpdrm in.self out.elf | ::usage: unself_gnpdrm in.self out.elf | ||
self_rebuilder | |||
:: usage: self_rebuilder [input.elf] [output.self] [original.self] [keytype] [keysuffix] [sdkversion] [sdktype] [auth id [idps.bin] [act.dat] [game.rif] | |||
:::self_rebuilder keytype keysuffix sdkversion sdktype input.elf output.self original.self | |||
:::input.elf=The input ELF/PRX to sign | |||
:::output.self=The output SELF/SPRX to generate | |||
:::original.self=The original SELF/SPRX for reference | |||
:::keytype=lv0|lv1|lv2|iso|app|ldr|npd (please note if type is ldr use versionsuffix retail) | |||
:::keysuffix=080|092|240|340|350|355|356|360|365|370 | |||
:::sdkversion=0.80.0|0.92.0|2.40.0|3.40.0|3.50.0|3.55.0|3.56.0|3.60.0|3.65.0|3.70.0 | |||
:::sdktype=0000:retail0|0001:retail|0002:retail1|0004|0007|000A|000D|0010|0013|0016|8000:devkit | |||
:::authid=1070000039000001 (only use if you want to change a revoked authid) | |||
:::idps.bin=The input idps.bin to use (only needed for NPD1/NPD2 de/encryption) | |||
:::act.dat=The input act.dat to use (only needed for NPD1/NPD2 de/encryption) | |||
:::game.rif=The input game.rif to use (only needed for NPD1/NPD2 de/encryption) | |||
==Geohot Signing Tools== | ==Geohot Signing Tools== | ||
| Line 84: | Line 377: | ||
::usage: package_finalize my.pkg | ::usage: package_finalize my.pkg | ||
==Graf Chokolo Tools== | == Graf Chokolo Tools == | ||
[http://github.com/grafchokolo/psgroove graftools] | [http://github.com/grafchokolo/psgroove graftools] | ||
[ | [[Talk:Graf%27s_PSGroove_Payload | Graftools]] | ||
:sendfile | :sendfile | ||
| Line 93: | Line 386: | ||
:pcap2bin | :pcap2bin | ||
: | == spkg tool 1.0 == | ||
*[[http://www.mirrorcreator.com/files/1KDUUGFL/spkg_tool.tar.gz_links|spkg (linux/win)]] | |||
requirements: | |||
* fail0verflow key folder | |||
* spkg(3.56+) and pkg(0.80-3.55) key/iv | |||
* disabled ecdsa check in spu_pkg_rvk_verifier | |||
<!--// spkg in.pkg out.spkg_hdr [-d|--decrypt_spkg_hdr_only] //--> | |||
usage:<br /> | |||
:spkg in.pkg out.spkg_hdr<br /> | |||
::or<br /> | |||
:spkg in.spkg_hdr out.decrypted_spkg -d | |||
== sputnik - Cell/SPU Pipeline viewer== | == sputnik - Cell/SPU Pipeline viewer== | ||
| Line 110: | Line 404: | ||
* [http://dl.dropbox.com/u/334837/Sputnik.exe.zip Windows] (will also need [http://qt.nokia.com/downloads QT runtime files]) | * [http://dl.dropbox.com/u/334837/Sputnik.exe.zip Windows] (will also need [http://qt.nokia.com/downloads QT runtime files]) | ||
* [http://dl.dropbox.com/u/334837/Sputnik.dmg MAC OSX] | * [http://dl.dropbox.com/u/334837/Sputnik.dmg MAC OSX] | ||
== commtool == | |||
Encryption/decryption of community files. | |||
Binaries: http://www.sendspace.com/file/ympcze | |||
Source code: http://www.sendspace.com/file/zjl6xx | |||
== netrpc == | == netrpc == | ||
| Line 143: | Line 443: | ||
objdump -d empty.o</pre> | objdump -d empty.o</pre> | ||
Source: http://askrprojects.net/software/objdump.html | Source: http://askrprojects.net/software/objdump.html | ||
=== doing SPRX === | |||
ppu-objdump -xD --endian=big --target=elf64-powerpc --architecture=powerpc:common64 --disassembler-options=cell --target=binary binary filename.elf | |||
== Several handy scripts == | == Several handy scripts == | ||
| Line 163: | Line 467: | ||
The returned value shouldn't be 0xff | The returned value shouldn't be 0xff | ||
ps3dm_um /dev/ps3dmproxy read_eprom 0x48C07 | ps3dm_um /dev/ps3dmproxy read_eprom 0x48C07 | ||
=== read eEID.sh === | |||
This script will dump your EID. | |||
echo Dumping EID | |||
dd if=/dev/ps3nflasha skip=$((0x2F000)) of=eid.bin bs=1 count=$((0x10000)) | |||
=== write eEID.sh === | |||
This script will write EID to flash. | |||
echo Writing EID | |||
dd if=eid.bin of=/dev/ps3nflasha bs=1 seek=$((0x2F000)) count=$((0x10000)) | |||
===dump_EID0.sh=== | ===dump_EID0.sh=== | ||
| Line 192: | Line 506: | ||
This will dump your NOR memory. | This will dump your NOR memory. | ||
echo Dumping nor | echo Dumping nor | ||
dd if=/dev/ps3nflasha of=nor.bin | dd if=/dev/ps3nflasha of=nor.bin bs=1024 | ||
===nor_write.sh=== | |||
This will write dump to NOR memory. | |||
echo Writing nor | |||
dd if=nor.bin of=/dev/ps3nflasha bs=1024 | |||
===dump_ram.sh=== | ===dump_ram.sh=== | ||
| Line 203: | Line 522: | ||
echo Dumping vram | echo Dumping vram | ||
dd if=/dev/ps3vram of=ps3vram.bin | dd if=/dev/ps3vram of=ps3vram.bin | ||
== Payloader3 == | == Payloader3 == | ||
* http:// | source code repository: | ||
* http://gitorious.ps3dev.net/payloader3/payloader3/trees/master | |||
<!-- | |||
* 2011-06-22 backup: http://gotbrew.org/payloader3.tar.gz / [http://www.multiupload.com/DM8KLHX2SS payloader3.tar.gz (55.55 MB)] | * 2011-06-22 backup: http://gotbrew.org/payloader3.tar.gz / [http://www.multiupload.com/DM8KLHX2SS payloader3.tar.gz (55.55 MB)] | ||
* Up including last commit before dashhacks went down : [http://www.multiupload.com/ZZ0X312CDM payloader3.tar.bz2 (45.49 MB)] (full git backup, also includes : [http://www.multiupload.com/EVO0GPP4DB payloader3-src-only.rar (2.08 MB)]) | * Up including last commit before dashhacks went down : [http://www.multiupload.com/ZZ0X312CDM payloader3.tar.bz2 (45.49 MB)] (full git backup, also includes : [http://www.multiupload.com/EVO0GPP4DB payloader3-src-only.rar (2.08 MB)]) | ||
--> | |||
===Howto=== | ===Howto=== | ||
| Line 227: | Line 548: | ||
=== ps3load 3.55 make_self fixed === | === ps3load 3.55 make_self fixed === | ||
* older versions of ps3load would '''not''' work on 3.50/3.55 (¨sysProcessExitSpawn2¨ won't work proper), and you had to use 3.41 instead. This is no longer an issue with the recent version ps3load which fixed the (make_self) issue for 3.55 | * older versions of ps3load would '''not''' work on 3.50/3.55 (¨sysProcessExitSpawn2¨ won't work proper), and you had to use 3.41 instead. This is no longer an issue with the recent version ps3load which fixed the (make_self) issue for 3.55 | ||
** standalone precompiled version to try: [http://www. | ** standalone precompiled version to try: [http://www.psdevwiki.com/files/devtools/payloader3/ps3load.gnpdrm.pkg ps3load.gnpdrm.pkg (522.17 KB)] (don't forget to delete your old version first) | ||
The PKG will install to the harddrive (dev_hdd0/game/PS3LOAD04/) with ps3load added as icon to the XMB > Network category. | The PKG will install to the harddrive (dev_hdd0/game/PS3LOAD04/) with ps3load added as icon to the XMB > Network category. | ||
| Line 303: | Line 624: | ||
346690: 80000000002be570 # syscall_map_open_desc | 346690: 80000000002be570 # syscall_map_open_desc | ||
== xorhack v2.0 == | |||
[http://www.multiupload.com/F09XP3YTVX xorhack_v2.0.zip (35.56 KB)] | |||
===Installing=== | |||
If you have a previous version of XorHack installed you should remove it first. Do this by navigating to the install dir and typing "make clean" then "make uninstall" and then delete all remaining source files. | |||
To install XorHack copy the all files and folders that came with this readme onto your PS3 harddrive and then navigate to the location you copied them to. | |||
Type "make" to build all parts of XorHack. | |||
Type "make install" to install all parts of XorHack. | |||
Type "make uninstall" to uninstall all parts of XorHack. | |||
=== Running === | |||
* Once installed you can start the exploit loop from the command line by typing "ps3exploit 100" to perform the exploit loop 100 times. | |||
* Once the exploit is successful the hypervisor can be dumped by typing "dumphv". It will dump it to a file in the current dir. | |||
* Once the exploit is successful the bootloader can be dumped by typing "dumpbl". It will dump it to a file in the current dir. | |||
== GameOS dumper tools == | |||
=== Memdump === | |||
<!--// also here [[Software_Dumping#Memdump]] //--> | |||
<div style="float:right">[[File:Memdump-lv1 1280.png|x300px|thumb|left|Memdump - lv1 screen]]</div> | |||
PS3 memory dumping tool that can dump lv1, lv2, NAND/NOR Flash, and eEID from GameOS. | |||
<gallery> | |||
File:Memdump-main 1280.png|Memdump - main screen | |||
File:Memdump-about 1280.png|Memdump - about screen | |||
File:Memdump-help 1280.png|Memdump - help screen | |||
File:Memdump-lv1 1280.png|Memdump - lv1 screen | |||
File:Memdump-lv2 1280.png|Memdump - lv2 screen | |||
</gallery> | |||
{{#ev:youtube|_uqCxkNxXqo}} | |||
==== Download ==== | |||
* [http://www.embedupload.com/?d=3HH5KJGLY4 memdump .pkg] | |||
* [https://archive.midnightchannel.net/SonyPS/PS3/Source%20Code/gitorious.ps3dev.net/memdump/ memdump source code] | |||
==== Applicable firmwares ==== | |||
{| class="wikitable" | |||
|- | |||
! rowspan="2" | FW !! rowspan="2" | lv1 !! rowspan="2" | lv2 !! rowspan="2" | Flash !! rowspan="2" | eEID !! colspan="2" | 0.01 FINAL | |||
|- | |||
! Logs !! Notes | |||
|- | |||
| style="background:lightgrey; color:#ff0000; text-align: center;" | <=2.60 {{CEX}} {{DEX}} || {{NA}} || {{NA}} || {{NA}} || {{NA}} || colspan="4" style="background:lightgrey; color:#ff0000; text-align: center;" | Not available as target version atm | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 2.70 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 2.76 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 2.80 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.00 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.01 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.10 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.15 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.20 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.21 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.30 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.40 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.41 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.42 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.50 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| style="background:Green; color:#ffffff; text-align: center;" | 3.55 {{CEX}} {{DEX}} || {{Yes}} || {{Yes}} || {{Yes}} || {{Yes}} || | |||
|- | |||
| 3.56 {{CEX}} {{DEX}} || {{Pending}} || {{Pending}} || {{Pending}} || {{Pending}} || | |||
|- | |||
| style="background:lightgrey; color:#ff0000; text-align: center;" | =>3.60 {{CEX}} {{DEX}} || {{NA}} || {{NA}} || {{NA}} || {{NA}} || rowspan="2" colspan="4" style="background:lightgrey; color:#ff0000; text-align: center;" | Not available as target version atm | |||
|- | |||
|} | |||
===== Legenda ===== | |||
* NA : Not Available as target version (mostly because of missing lv1:mmap114 or lv2:peek/poke patches) | |||
* Yes: Fully supported | |||
* No: Not supported | |||
* Partial: Some functions work, others might not be complete | |||
* Pending: No reports yet (help out by sending in your logs and dumps in a ZIP/RAR/7z!) | |||
==== Known bugs ==== | |||
* buttons do not come back up after pressing -> to be fixed in v0.02 (button handler thread) | |||
* exit app gives rightscreen black triangle -> to be fixed in v0.02 (cleanup RSX buffer) | |||
* when free space is 0 bytes when dumping, application will halt -> to be fixed in v0.02 (check freespace first) | |||
==== Current limitations ==== | |||
* Needs mmap114+peek/poke as minimal patches | |||
* Can be buggy with strange spoofs | |||
* No reports yet on Kiosk/SEX & Tool/DECR models | |||
* NAND only : second bootldr at 0xF000000 - 0xF03FFFF (The last 256KB of flash) will be missing. Just copypaste the first bootldr 0x0000000 - 0x003FFFF (The first 256KB of flash), they are the same. Also, a console boots fine with only the first one. | |||
=== flash dumper === | |||
precompiled: | |||
* [http://www.psdevwiki.com/files/flash/Tools/USB%20Flash%20Dump/dump_flash.pkg dump_flash.pkg (70.48 KB)] | |||
<!--// * [http://www.multiupload.com/2V5J0MHF4F dump_flash-faster.pkg (70.23 KB)] not faster, old bugged version that also dumps vflash on NOR consoles //--> | |||
:NOR flash - dump will take about 30 minutes<!--// 30mins and 20 secs ~9 KB/sec //-->, size: 16 MB (1 file: flash.bin) | |||
:NAND flash - dumps will take more then 2½ hours<!--// 150mins ~ 27 KB/sec //-->, size: 239MB (1 file: flash.bin) with bootldr missing. | |||
* [http://www.multiupload.com/VWN0XF3LFZ dump_flash_ptab.pkg (70.23 KB)] | |||
:NOR flash - The tool dumps the first 2 sectors of "VFLASH partition table" located inside "virtual flash" region on HDD, dump size 0x3FF (0x30 header + 0x90 per region) | |||
git source: | |||
* [http://foxbrew.org/git/otheros-utils/dump_flash.git/ dump_flash.git] | |||
* [http://foxbrew.org/git/otheros-utils/dump_flash_ptab.git/ dump_flash_ptab.git] | |||
* [http://www.psdevwiki.com/files/flash/Tools/USB%20Flash%20Dump/dump_flash-src.rar dump_flash-src.rar] | |||
=== lv1 dumper === | |||
precompiled: | |||
* [http://www.multiupload.com/FJTQM8QAY2 dump_lv1.pkg (70.11 KB)] (glevand)<br /> | |||
:lv1 dump will take about 30minutes, size: 16 MB (1 file: lv1.bin) | |||
git source: | |||
* [http://foxbrew.org/git/otheros-utils/dump_lv1.git/ dump_lv1.git] | |||
alternative: | |||
* lv1dumper [http://www.multiupload.com/WVLKP4MHS4 FLU1_T_2011.zip (9.72 KB)] (flukes1) | |||
:This is an application which runs on the PS3 that you can compile and package using PSL1GHT and geohot’s tools. After running it, lv1 will be mapped at 0×8000000014000000 with read/write access, and you will be able to poke lv2 without the system shutting down. | |||
=== lv2 dumper === | |||
precompiled: | |||
* [http://www.multiupload.com/J0V1AIZKT0 dump_lv2.pkg (70.11 KB)] (glevand)<br /> | |||
:lv2 dump will take considerable less than lv1dump, size: 8.5 MB (2 files: lv2.bin.0 & lv2.bin.1) | |||
* [http://www.multiupload.com/MBEP4VSCN5 lv2dump_07a.pkg (1.48 MB)] (other) <br /> | |||
:lv2 dump saves to harddrive, you'll have to ftp it out. no sourcecode available. | |||
git source: | |||
* [http://foxbrew.org/git/otheros-utils/dump_lv2.git/ dump_lv2.git] | |||
=== sysrom dumper === | |||
precompiled: | |||
[http://www.multiupload.com/27TV582N4O dump_sysrom.pkg (69.67 KB)] (glevand)<br /> | |||
:sysrom dump takes only few seconds, size: 256KB (1 file: sysrom.bin) | |||
git source: | |||
* [http://foxbrew.org/git/otheros-utils/dump_sysrom.git/ dump_sysrom.git] | |||
=== metldrdumper === | |||
precompiled: | |||
[https://mega.nz/#!Yk1RiYyT!xbNV_ZbPLatBtw3M_9DwORz2HXGCiso4gGRE0tVQhOY dump_metldr.pkg (69.67 KB)] (CMX / original source code by: Flatz)<br /> | |||
:metldr dump takes only few seconds, size: 256KB (1 file: dump.bin) | |||
source code: | |||
* [https://mega.nz/#!YkNk1DzS!k9bCVXTYlx1gexoOJIx7TfH8uQ0C3gGigO_e2W70tEM metldr_dumper] | |||
=== vflash dumper === | |||
git source: | |||
* [http://foxbrew.org/git/otheros-utils/dump_vflash_ptab_fat.git/ dump_vflash_ptab_fat.git] | |||
* [http://foxbrew.org/git/otheros-utils/dump_vflash_ptab_slim.git/ dump_vflash_ptab_slim.git] | |||
=== vsh dumper === | |||
precompiled: | |||
* [http://www.multiupload.com/IBF5XTDFWP vshDumper.rar (25.29 KB)] ([[User:Daxgr]])<br /> | |||
:([http://pastie.org/private/lbv2vc50spgjx816mahfa IDA analysis of sacd.sprx]) | |||
== pupx dev_flash == | |||
Extracts dev_flash files from ps3 updates. To extract them you just have to put PS3UPDAT.PUP in the same folder and launch it. | |||
*http://hsreina.shadosoft-tm.com | |||
*http://psx-scene.com/forums/f149/extract-dev_flash-ps3-update-74664/ | |||
*http://www.multiup.org/download/4884407dbbdc793549561d0d735ba8b1/pupx_dev_flash.rar | |||
== dev_flash and dev_flash3 unpacker == | == dev_flash and dev_flash3 unpacker == | ||
it's a simple dev_flash extractor for 3.56+ PUPs | it's a simple dev_flash extractor for 3.56+ PUPs | ||
http://pastebin.com/ | Before using it: Change this line "TOOLS=/home/wargio/.ps3tools" with the path of your tools, example: TOOLS=/home/god/ps3dev/ps3tools | ||
LINUX version: http://pastebin.com/kLrPFb7y | |||
OSX version: http://pastebin.com/FDMbgyVk | |||
Usage: unpack_dev_flash.sh <*.pup> | |||
example: unpack_dev_flash.sh PS3UPDAT.PUP | |||
== core os extractor == | |||
it's a simple core os extractor for 3.56+ PUPs | |||
Before using it: Change this line "TOOLS=/home/wargio/.ps3tools" with the path of your tools, example: TOOLS=/home/god/ps3dev/ps3tools | |||
Linux/OSX: http://pastebin.com/1AkEgW3y | |||
Usage: ./extract_coreos.sh <PUP> | |||
example: extract_coreos.sh PS3UPDAT.PUP | |||
== Syscon FW Reader == | |||
This simple program will read and show information about a Syscon Firmware package.<br /> | |||
To compile it, just run make.<br /> | |||
[http://gitorious.ps3dev.net/playstation-3/ps3tools SRC] | |||
== SFO Reader == | |||
it will show useful informations, built initially for vita pkgs<br /> | |||
To build it, just run make.<br /> | |||
[http://gitorious.ps3dev.net/playstation-3/ps3tools SRC] -> [[Gitorious]] | |||
Example of output: | |||
<pre>[SFO HDR] 0x46535000 | |||
[SFO Version] 0x00000101 | |||
[SFO N] 13 Value(s) | |||
[SFO Values] 0x000000e4 | |||
[SFO Params] 0x0000016c | |||
[ SFO ] | |||
[ 1 ] APP_VER | Param: 01.00 | |||
[ 2 ] ATTRIBUTE | Param: 0x0 | |||
[ 3 ] BOOTABLE | Param: 0x1 | |||
[ 4 ] CATEGORY | Param: AV | |||
[ 5 ] LICENSE | Param: Library programs ©Sony Computer Entertainment Inc. Licensed for play on the PLAYSTATION®3 Computer Entertainment System or authorized PLAYSTATION®3 format systems. For full terms and conditions see the user's manual. This product is authorized and produced under license from Sony Computer Entertainment Inc. Use is subject to the copyright laws and the terms and conditions of the user's license. | |||
[ 6 ] PARENTAL_LEVEL | Param: 0x1 | |||
[ 7 ] PS3_SYSTEM_VER | Param: 03.4200 | |||
[ 8 ] REGION_DENY | Param: 0xfffffffd | |||
[ 9 ] RESOLUTION | Param: 0x1d | |||
[ 10 ] SOUND_FORMAT | Param: 0x307 | |||
[ 11 ] TITLE | Param: Netflix Instant Streaming | |||
[ 12 ] TITLE_ID | Param: NPUP00030 | |||
[ 13 ] VERSION | Param: 01.03 | |||
</pre> | |||
==SFO2SFX== | |||
it's a really simple Sfo to sfx converter.<br />for now it's not able to convert from sfx to sfo (when i will have more time, i will write a SFX2SFO. deroad)<br /> | |||
Download [http://www.mediafire.com/?u198mdksubj6c9c ps3tool_with_sfo2sfx] (this is my full SRC. all the tools are already compiled)<br /> | |||
[http://gitorious.ps3dev.net/playstation-3/ps3tools Mirror]<br /> | |||
From<br /> | |||
<pre>[SFO HDR] 0x00505346 | |||
[SFO Version] 0x00000101 | |||
[SFO N] 6 Value(s) | |||
[SFO Params Offsets] 0x000000b4 | |||
[ SFO ] | |||
[ 1 ] CATEGORY | Param: 2D | |||
[ 2 ] PARENTAL_LEVEL | Param: 0x1 | |||
[ 3 ] PS3_SYSTEM_VER | Param: 01.3100 | |||
[ 4 ] TITLE | Param: PS2 System Data | |||
[ 5 ] TITLE_ID | Param: NPIA00001 | |||
[ 6 ] VERSION | Param: 01.00</pre> | |||
to<br /> | |||
<pre><?xml version="1" encoding="utf-8" standalone=yes"?> | |||
<paramsfo add_hidden="false"> | |||
<param key="CATEGORY" fmt="utf8" max_len="4">2D</param> | |||
<param key="PARENTAL_LEVEL" fmt="int32" max_len="4">1</param> | |||
<param key="PS3_SYSTEM_VER" fmt="utf8" max_len="8">01.3100</param> | |||
<param key="TITLE" fmt="utf8" max_len="128">PS2 System Data</param> | |||
<param key="TITLE_ID" fmt="utf8" max_len="16">NPIA00001</param> | |||
<param key="VERSION" fmt="utf8" max_len="8">01.00</param> | |||
</paramsfo></pre> | |||
==make_his== | |||
Generates a PARAM.HIS file from a Unix-formatted text file | |||
https://github.com/jjolano/make_his | |||
==HIP2HIS== | |||
This app simply convert a PARAM.HIP file to PARAM.HIS | |||
http://www.mediafire.com/?rv6jajz3nfy53iw | |||
== ReactPSN .rap to .rif converter == | |||
This tool will convert .rap files to .rif. Place it to the ps3tools directory along with other tools and then place your idps and act.dat files to appropriate folders. | |||
::usage: rap2rif <rap file> <rif file> | |||
* [http://www.mediafire.com/?sgxq5r7twy9907d '''Rap2Rif''' compiled executable by '''Flatz'''] | |||
* [https://web.archive.org/web/20141118183315/http://pastie.org/private/yltlfwubsz8w5pyhmojyfg '''Rap2Rif''' source code by '''Flatz'''] | |||
==ReactPSN .rif -> .rap converter== | |||
Your concole's IDPS named idps is in the exdata file folder.<br /> | |||
Your act.dat is also in the exdata file folder.<br /> | |||
The usage:<br /> | |||
rif2rap <xxx.rif> <xxx.rap> | |||
or | |||
rif2rap <xxx.rif> | |||
http://www.mirrorcreator.com/files/SGL6EZCS/rif2rap.rar_links | |||
== .rifkey to ReactPSN .rap converter == | |||
This tool can convert rifkey (klicensee) file to .rap file. | |||
rifkey2rap <rifkey file> <rap file> | |||
* [http://mir.cr/1QRV777I ''Rifkey2Rap''' compiled executable + souce code by '''Flatz'''] | |||
* [https://web.archive.org/web/20141118220924/http://pastie.org/private/9hjpnaewxg5twytosnx4w ''Rifkey2Rap''' souce code by '''Flatz'''] | |||
== ReactPSN .rap to .rifkey converter == | |||
This tool can convert .rap file to rifkey (klicensee) file. | |||
rap2rifkey <rap file> <rifkey file> | |||
* [https://web.archive.org/web/20141118183317/http://pastie.org/private/pmnmsnqg6zbfnk9xactbw '''Rap2Rifkey''' souce code by '''Flatz'''] | |||
== Metldr extractor == | |||
Extract metldr of NOR/NAND dump. | |||
usage: extract_metldr <flash.bin> <destination> | |||
[http://gitorious.ps3dev.net/simple-ps3-tools/metldr_extractor/trees/master Source] | |||
(or just use Flowrebuilder and extract all binary) | |||
== decompile/disassembly .NET== | |||
* http://ilspy.net/ | |||
* http://www.devextras.com/decompiler/ | |||
* http://www.jetbrains.com/decompiler/ | |||
* http://www.telerik.com/products/decompiler.aspx | |||
* http://www.reflector.net/ | |||
== Total Commander == | |||
* Handy for searching static values (such as sboxes or curves) recursively in folders | |||
* Also useful to know where keys exist (in which elf they are located) | |||
* http://www.ghisler.com/ | |||
== PkgView == | |||
* By ifcaro, [http://ps3zone.ifcaro.net/ web], [https://github.com/ifcaro/PkgView source code] | |||
== SPRXPatcher == | |||
* A modern PlayStation 3 ELF patcher to load SPRX files | |||
* [https://github.com/NotNite/SPRXPatcher Source code] | |||
{{Development}}<noinclude>[[Category:Main]]</noinclude> | |||
Latest revision as of 02:01, 14 August 2024
Tools[edit | edit source]
Git[edit | edit source]
SceTool[edit | edit source]
- scetool / [1] (Windows)
- cygwin-dll.rar (needed in case of cygwin1.dll missing error)
- scetool_0.2.9.7z (Linux)
- scetool_0.2.9 (OSX)
common for all above: keys
scetool 0.2.7 <public build> (C) 2011-2012 by naehrwert NP local license handling (C) 2012 by flatz
Setup[edit | edit source]
- /data/keys : Keyfile. - /data/ldr_curves : Loader curves (7744 bytes). - /data/vsh_curves : VSH curves (360 bytes). - /data/idps : IDPS as binary file - /data/act.dat : act.dat - /rifs/* : *.rif files - /raps/* : *.rap files
Keyfile format[edit | edit source]
[keyname]
type={SELF, RVK, PKG, SPP, OTHER}
revision={00, ..., 18, 8000}
version={..., 0001000000000000, ...}
self_type={LV0, LV1, LV2, APP, ISO, LDR, UNK_7, NPDRM}
key=...
erk=...
riv=...
pub=...
priv=...
ctype=...
Keyset example[edit | edit source]
[metldr] type=SELF revision=00 self_type=LDR erk=0000000000000000000000000000000000000000000000000000000000000000 riv=00000000000000000000000000000000 pub=00000000000000000000000000000000000000000000000000000000000000000000000000000000 priv=000000000000000000000000000000000000000000 ctype=00
NPDRM key(set) names[edit | edit source]
- [NP_tid]: Title ID OMAC1 key. - [NP_ci]: Control info OMAC1 key. - [NP_klic_free]: Free klicensee. - [NP_klic_key]: klicensee key. - [NP_idps_const]: IDPS constant. - [NP_rif_key]: rif key. - [NP_sig]: Footer signature ECDSA keyset.
Error: Could not find keyset for SELF[edit | edit source]
Unlike unself, scetool does not bruteforce keys. So if you are trying to decrypt a file that is using a 4.75 key (4.20-4.92) and you only have that same key under :
4.20 · 4.21 · 4.22 · 4.23 · 4.25 · 4.26 · 4.30 · 4.31 · 4.40 · 4.41 · 4.45 · 4.46 · 4.50 · 4.55 · 4.60 · 4.65 · 4.66 · 4.70
it will error out. To see which key version is used by that complaining SELF, use:
scetool -i file_in
and add the missing key(s)
if that produces a line like:
Key Revision [DEBUG]
the file is an fself (debug == no keys), just strip the first 0x90 bytes and save
Help text[edit | edit source]
USAGE: scetool [options] command
Commands[edit | edit source]
COMMANDS Parameters Explanation -h, --help Print this help. -k, --print-keys List keys. -i, --print-infos file_in Print SCE file info. -d, --decrypt file_in file_out Decrypt/dump SCE file. -e, --encrypt file_in file_out Encrypt/create SCE file.
Options[edit | edit source]
OPTIONS Possible Values Explanation -v, --verbose Enable verbose output. -r, --raw Enable raw value output. -0, --sce-type SELF/RVK/PKG/SPP SCE File Type -1, --compress-data TRUE/FALSE(default) Whether to compress data or not. -s, --skip-sections TRUE(default)/FALSE Whether to skip sections or not. -2, --key-revision e.g. 00,01,...,0A,... Key Revision -m, --meta-info Use provided meta info to decrypt. -3, --self-auth-id e.g. 1010000001000003 Program Authority ID -4, --self-vendor-id e.g. 01000002 Program Vender ID -5, --self-type LV0/LV1/LV2/APP/ISO/ LDR/NPDRM Program Type -6, --self-fw-version e.g. 0003004100000000 Firmware Version -7, --self-add-shdrs TRUE(default)/FALSE Whether to add ELF shdrs or not. -8, --self-ctrl-flags 32 bytes Override control flags. -9, --self-cap-flags 32 bytes Override capability flags. -b, --np-license-type LOCAL/FREE License Type -c, --np-app-type SPRX/EXEC/UPDATE App Type -f, --np-content-id Content ID -l, --np-klicensee 16 bytes Override klicensee. -g, --np-real-fname e.g. EBOOT.BIN Real Filename -j, --np-add-sig TRUE/FALSE(default) Whether to add a NP sig. or not.
History[edit | edit source]
Version 0.2.7[edit | edit source]
- Added local NP license handling. - Added option to override klicensee. - Added option to disable section skipping (in SELF generation).
Version 0.2.5[edit | edit source]
- Added option to use provided metadata info for decryption. - "PS3" path environment variable will now be searched for keys/ldr_curves/vsh_curves too.
Version 0.2.4[edit | edit source]
- Added option to display raw values. - Moved factory Auth-IDs to <public build> (as they are on psdevwiki now).
Version 0.2.2[edit | edit source]
- Added options to override control/capability flags (32 bytes each). - Fixed where a false keyset would crash scetool when decrypting a file. - Some source level changes and optimizations.
Version 0.2.1[edit | edit source]
- zlib [2] is required to use scetool. - 'sdk_type' was changed to 'revision' in data/keys.
OpenSCETool[edit | edit source]
https://github.com/spacemanspiff/oscetool
Break N Make (MakeSelf & BreakSelf)[edit | edit source]
Download[edit | edit source]
Download: https://www.mediafire.com/?f9aaj86vn0w4nn1 mirror
Key.conf[edit | edit source]
http://pastie.org/9821745 <- dead link
Features[edit | edit source]
- Win32 GUI Version
- Drag and Drop of bin.self.SPRX (Will Open if Klic Key needs changing)
- Changing of Decyption Klic
- Decryption of NPDRM
- Uses Key.conf to add new Keys if necessary (iso/app/npdrm/lv0/lv1/lv2 keys)
- Can be added (Manually) to Right click Function for Quick Decryption
Changelog[edit | edit source]
V1.1 (08-11-2014)[edit | edit source]
- Added Control Flags 0x1B = 0x10
- Changed Wording For Flag "default licensee" to First Boot..
- Moved Configuration Section into its own Button
- Now you can set the Configuration for the ini files inside
- Added in klicensee.ini
- This allows you to Database your own Personal Keys.
- Added ability to Change DRM Type
- Checks for it in the klicensee.ini will set new key if pressent
- Added Quick Selector
- (Reads from klicensee.ini) in NPDRM Settings Area for any preprogramed files..
- Added Drag and Drop to Clone
- (Can now Drop file you want to use for Clone "ANY" place outside of the Elf/Self File Sections and it will read it to try and clone it)
- Upgraded Clone Function (this will use klicensee.ini)
- If the file is present inside the klicensee.ini it will auto detect when you Clone the original file.
New Klicensee.ini what is it?[edit | edit source]
First Format
[klicensee] title= productid= filename= flags= key0= key1= key2= key3= key4= [/klicensee]
Explaination
- title =
is the title you will see in Quick Selection area. (Put what you would like)
- productionid =
this is the 36character ID that belongs to the game (eg: UP1017-BLUS30682_00-GTACOMPLETEV0102)
- filename =
the name to the file this works for so Eboot/SPRX/SELF and so on) (note 1 name per [klicensee] section)
- flags =
20 Game Update / 01 First boot . Note that they Stack so 21 both on
- Key0=
Disc (normaly just normal Free key no need to put)
- Key1=
Network (Normaly the same as RiF key)
- Key2=
Local (This is your Personal Rif key)
- Key3=
Free (for Eboots this key is the normal Free key, for Sprx,Selfs this key can be found inside the Eboot to decypt the Sprx,Self)
- Key4=
for PSP
Note : you only need to put the Key section you plan to use.
here is an example setup
[klicensee] title=GTACOMPLETE SELF productid=UP1017-BLUS30682_00-GTACOMPLETEV0102 filename=GTAIV.self key3= 00000000000000000000000000000000 [/klicensee]
V1.0 - Original (29-10-2011)[edit | edit source]
- Allows you to Encrypt (Dex)+(CEX)+(NPDRM) Bin,Self,Sprx,Isoself
- Has Clone Function
- Allows for Multi control over how files are encrypted ..
- Allows for Setup of Quick Settings inside Quick.ini
- Updatable keys.conf uses same one as Breakself.
- Allows for Encrypting Using original
What is Clone?[edit | edit source]
- Clone Settings from Original Encrypted file
Press Clone Settings then pick original Encrypted file .. If NPDRM you may need to fill in the K_Licensee with decrypt key Before doing the Clone..
NPDTool v4d[edit | edit source]
npdtool v4d by belmondo and user ©2014
usage decrypt: npdtool [mode] infile outfile [rap/idps/klic] [act] [rif]
[mode]: d (decrypt edata using idps, act.dat and rif)
dk (decrypt edata using k_licensee)
dr (decrypt edata using rap)
ds (decrypt sdata)
usage encrypt edata: npdtool [format] infile outfile [klic] [cID] [block]
[format]: 1 (format1 edata)
1c (format1 compressed edata)
2 (format2 edata)
2c (format2 compressed edata)
3 (format3 edata)
3c (format3 compressed edata)
4 (format4 edata)
4c (format4 compressed edata)
[cID]: XX0000-YYYY00000_00-0000000000000000
[block]: not for compressed [MAX 8000]
usage encrypt goma: npdtool [format] [cID]
[format]: goma (licence edata)
[cID]: XX0000-YYYY00000_00-0000000000000000
usage encrypt sdata: npdtool [format] infile outfile [block]
[format]: 1s (format1 sdata)
2s (format2 sdata)
2sc (format2 compressed sdata)
3s (format3 sdata)
3sc (format3 compressed sdata)
4s (format4 sdata)
4sc (format4 compressed sdata)
[block]: not for compressed [MAX 8000]
usage bruteforce: npdtool [mode] inNPD inELF outK_lic.bin
[mode]: b (bruteforce k_licensee in hex)
b2 (bruteforce k_licensee in ascii)
usage info: npdtool [mode] inNPD
[mode]: i (info)
PSNope[edit | edit source]
by u$er - latest version 1.06?
PSN Patch[edit | edit source]
(psidpatch+psnope)
- http://store.brewology.com/ahomebrew.php?brewid=244 v4.70.06 by KW
SDATA Tool[edit | edit source]
Small open source tool to unpack and decrypt SDATA files. All the hard work and reverse engineering done by Hykem, along with collaboration of AlexAltea and BlackDaemon. It supports all SDATA file variants: v1 to v4, compresed or uncompressed, debug or release SDATAs.
Link: https://github.com/inaina/sdata-tool
Usage: sdata-tool.exe <input> <output>
fail0VERFLOW[edit | edit source]
- cospkg
- usage: cospkg cos.pkg dir
- cosunpkg
- usage: cosunpkg filename.pkg target
- pkg
- usage: pkg [key suffix] [contents] [filename.pkg]
- unpkg
- usage: unpkg [-s] filename.pkg target
- readself
- usage: readself file.self
- readselfoffsets
- usage: readselfoffsets file.self
- unself
- usage: unself in.self out.elf
- makeself
- usage: makeself [-c] [type] [version suffix] [version] [vendor id] [auth id] [sdk type] [elf] [self]
- makeself keytype keysuffix sdkversion vendorid authid sdktype file.elf file.self
- keytype=lv0|lv1|lv2|iso|app|ldr
- keysuffix=315|331|341|355
- sdkversion=3.15.0|3.41.0|3.55.0
- vendorid=01000002
- authid=1070000039000001
- sdktype=0000:retail0, 0001:retail, 0002:retail1, 8000 devkit
- usage: makeself [-c] [type] [version suffix] [version] [vendor id] [auth id] [sdk type] [elf] [self]
- puppack
- usage: puppack filename.pup directory [build number]
- pupunpack
- usage: pupunpack filename.pup directory
- norunpack
- usage: norunpack dump.b directory
- sceverify
- usage: sceverify filename
- SCEkrit
- usage: scesekrit filename1 filename2
unself_gnpdrm.c source & unself_gnpdrm.exe Win32 compile : unself_gnpdrm.rar (60.16 KB)
- unself_gnpdrm
- usage: unself_gnpdrm in.self out.elf
self_rebuilder
- usage: self_rebuilder [input.elf] [output.self] [original.self] [keytype] [keysuffix] [sdkversion] [sdktype] [auth id [idps.bin] [act.dat] [game.rif]
- self_rebuilder keytype keysuffix sdkversion sdktype input.elf output.self original.self
- input.elf=The input ELF/PRX to sign
- output.self=The output SELF/SPRX to generate
- original.self=The original SELF/SPRX for reference
- keytype=lv0|lv1|lv2|iso|app|ldr|npd (please note if type is ldr use versionsuffix retail)
- keysuffix=080|092|240|340|350|355|356|360|365|370
- sdkversion=0.80.0|0.92.0|2.40.0|3.40.0|3.50.0|3.55.0|3.56.0|3.60.0|3.65.0|3.70.0
- sdktype=0000:retail0|0001:retail|0002:retail1|0004|0007|000A|000D|0010|0013|0016|8000:devkit
- authid=1070000039000001 (only use if you want to change a revoked authid)
- idps.bin=The input idps.bin to use (only needed for NPD1/NPD2 de/encryption)
- act.dat=The input act.dat to use (only needed for NPD1/NPD2 de/encryption)
- game.rif=The input game.rif to use (only needed for NPD1/NPD2 de/encryption)
- usage: self_rebuilder [input.elf] [output.self] [original.self] [keytype] [keysuffix] [sdkversion] [sdktype] [auth id [idps.bin] [act.dat] [game.rif]
Geohot Signing Tools[edit | edit source]
- make_self
- usage: make_self input.elf output.self
- make_self_npdrm
- usage: make_self_npdrm input.elf output.self <content_id>
- warning NPDRM cares about the output file name, do not rename
- package_finalize
- usage: package_finalize my.pkg
Graf Chokolo Tools[edit | edit source]
- sendfile
- pcap2bin
spkg tool 1.0[edit | edit source]
requirements:
- fail0verflow key folder
- spkg(3.56+) and pkg(0.80-3.55) key/iv
- disabled ecdsa check in spu_pkg_rvk_verifier
usage:
- spkg in.pkg out.spkg_hdr
- or
- or
- spkg in.spkg_hdr out.decrypted_spkg -d
sputnik - Cell/SPU Pipeline viewer[edit | edit source]
http://www.ps3hax.net/2011/08/sputnik-build-3-cellspu-pipeline-viewer/
- Windows (will also need QT runtime files)
- MAC OSX
commtool[edit | edit source]
Encryption/decryption of community files. Binaries: http://www.sendspace.com/file/ympcze Source code: http://www.sendspace.com/file/zjl6xx
netrpc[edit | edit source]
git://gist.github.com/1041214.git
https://gist.github.com/1041214
Objdump[edit | edit source]
If you, for whatever reason, need to disassemble non-x86 binary files, you usually look out for a disassembler. If there's nothing free available for your platform (e.g.: ARM) one of the few solutions may be buying something like IDA Pro.
But wait, if you only need to "analyze" a small portion (boot-sector, single routine, ...) and someone already ported GNUs GCC and bintools to your platform, using OBJDUMP may do the trick...
If "raw.bin" is your binary file, just typing
objdump -d raw.bin objdump: raw.bin: File format not recognized
will not work. Objdump needs a file system object or file.
Just do it like this:
# create an empty file touch empty.c # compile this empty file gcc -c -o empty.o empty.c # add binary as a raw section objcopy --add-section raw=raw.bin empty.o # remove ".comment" section to join objcopy -R .comment empty.o # now run objdump on it objdump -d empty.o
Source: http://askrprojects.net/software/objdump.html
doing SPRX[edit | edit source]
ppu-objdump -xD --endian=big --target=elf64-powerpc --architecture=powerpc:common64 --disassembler-options=cell --target=binary binary filename.elf
Several handy scripts[edit | edit source]
Most of the scripts are using graf's ps3dm-utils, so make sure you have them in your /bin directory. Also make sure you are using graf's kernel (graf_chokolo kernel 2.6.39).
panic1.sh[edit | edit source]
This script will panic lv1 and get you back to petitboot, without exiting to GameOS.
ps3hvc_hvcall /dev/ps3hvc panic 1
usb_dongle_auth.sh[edit | edit source]
This script will get you into Factory/Service mode, without using dongle:
echo Generating a challenge ps3dm_usb_dongle_auth /dev/ps3dmproxy gen_challenge echo Generating a response '(0xAAAA)' ps3dm_usb_dongle_auth /dev/ps3dmproxy gen_resp 0xAAAA echo Verifying response '(0xAAAA)' ps3dm_usb_dongle_auth /dev/ps3dmproxy verify_resp 0xAAAA echo Checking if 'Product Mode is enabled The returned value shouldn't be 0xff ps3dm_um /dev/ps3dmproxy read_eprom 0x48C07
read eEID.sh[edit | edit source]
This script will dump your EID.
echo Dumping EID dd if=/dev/ps3nflasha skip=$((0x2F000)) of=eid.bin bs=1 count=$((0x10000))
write eEID.sh[edit | edit source]
This script will write EID to flash.
echo Writing EID dd if=eid.bin of=/dev/ps3nflasha bs=1 seek=$((0x2F000)) count=$((0x10000))
dump_EID0.sh[edit | edit source]
This script will dump your EID0.
echo Dumping EID0 ps3dm_iim /dev/ps3dmproxy get_data 0x0 > EID0.bin
dump_EID4.sh[edit | edit source]
This script will dump your EID4.
echo Dumping EID4 ps3dm_iim /dev/ps3dmproxy get_data 0x4 > EID4.bin
get_EID0_size.sh[edit | edit source]
This script will get the size of your EID0.
echo EID0 size: ps3dm_iim /dev/ps3dmproxy get_data_size 0x0
get_EID4_size.sh[edit | edit source]
This script will get the size of your EID4.
echo EID4 size: ps3dm_iim /dev/ps3dmproxy get_data_size 0x4
get_metldr_size.sh[edit | edit source]
This script will get the size of metldr.
echo metldr size: ps3dm_iim /dev/ps3dmproxy get_data_size 0x1000
nor_dump.sh[edit | edit source]
This will dump your NOR memory.
echo Dumping nor dd if=/dev/ps3nflasha of=nor.bin bs=1024
nor_write.sh[edit | edit source]
This will write dump to NOR memory.
echo Writing nor dd if=nor.bin of=/dev/ps3nflasha bs=1024
dump_ram.sh[edit | edit source]
This script will dump your ram.
echo Dumping ram dd if=/dev/ps3ram of=ps3ram.bin
dump_vram.sh[edit | edit source]
This script will dump your vram.
echo Dumping vram dd if=/dev/ps3vram of=ps3vram.bin
Payloader3[edit | edit source]
source code repository:
Howto[edit | edit source]
- Set firmware version in Makefile
- Compile with "./build.sh"
- Copy pkg file to usb stick
- Install pkg on PS3
Precompiles[edit | edit source]
Notes[edit | edit source]
- Loading ps3load after the payload will execute the appropriate ps3load.self, after your self exits you will be returned to the XMB.
- Loading 'ethdebug' will load ArielX's Kammy self, after it executes you will be returned to the XMB.
- Loading 'ethdebug/ps3load' will load ethdebug, then ps3load.
ps3load 3.55 make_self fixed[edit | edit source]
- older versions of ps3load would not work on 3.50/3.55 (¨sysProcessExitSpawn2¨ won't work proper), and you had to use 3.41 instead. This is no longer an issue with the recent version ps3load which fixed the (make_self) issue for 3.55
- standalone precompiled version to try: ps3load.gnpdrm.pkg (522.17 KB) (don't forget to delete your old version first)
The PKG will install to the harddrive (dev_hdd0/game/PS3LOAD04/) with ps3load added as icon to the XMB > Network category.
Using ps3load[edit | edit source]
- make your app, produce at least an ELF
- sprxlinker yourapp.elf (this should be done for you if you use any of the samples)
- make_self yourapp.elf yourapp.self
- load ps3load on the PS3
- define the PS3LOAD environment variable in your favorite shell with tcp:ip_addr (where ip_addr is your the ip address of your PS3)
- ps3load yourapp.self
lv2-v9.pkg[edit | edit source]
patch1[edit | edit source]
# PL3 3.55 # Patches marked with (*1) seem to be unstable. Thanks to drizztbsd and # RandomUse. # PL3: ef48: payload.bin # Segment 0: ### 24e44: 38600000 # patch_func6 *1 55dc4: 38600000 # lv2open: patch_func8_offset1 55f28: 60000000 # lv2open: patch_func8_offset2 ### 79d80: 3880000090830000 # patch_func4 + patch_func4_offset *1 ### 79d88: 4E800020 # cont'd *1 ### 7af7c: 60000000 # patch_func9_offset *1 ### c1dd0: 38600000 # patch_func7 *1 2b3298: 4BD5C050 # hook_open (patch_func3 + patch_func3_offset) # Segment 1: 346688: 800000000000f2dc # syscall_map_open_desc # Spoof # *f3b8: version.bin # 2e8218: 800000000000f378 # syscall_versiontest # 2e82f0: 800000000000f3c0 # syscall_process_sdkversion # 16ad74: 3960000a44000002 # sha1 test # f3e4: find 3437353136000000 # *fe34: 3436313335000000
patch2[edit | edit source]
# Waninkoko V2 # 3270: e8821030e87c0020 # load unsigned ELFs # 3278: f8640000 # e7f0: 48000c50 # Some jump ef48: payload2.bin 19360: 7c001fac4c00012c 1936c: 7c0018ac7c0004ac 24e44: 4bfea5c5 # patch_func6 55dc4: 38600000 # patch_func8_offset1 55f28: 60000000 # patch_func8_offset2 79d80: 38800000908300004e800020 # patch_func4 + patch_func4_offset *1 7af7c: 60000000 # patch_func9_offset c1dd0: 4bf4d639 # patch_func7 2b3298: 4bd5bf40 # hook_open 3465b0: 80000000002e81e8 # sc8 346688: 8000000000324968 # sc35
patch3[edit | edit source]
# Syscall36 # by 2 anonymous people 55f14: 60000000 55f1c: 48000098 7af68: 60000000 7af7c: 60000000 2be4a0: payload3.bin 2b3274: 4800b32c2ba30420 # add a jump to payload2_start 55EA0: 63FF003D60000000 # fix 8001003D error 55F64: 3FE080013BE00000 # fix 8001003E error 346690: 80000000002be570 # syscall_map_open_desc
xorhack v2.0[edit | edit source]
Installing[edit | edit source]
If you have a previous version of XorHack installed you should remove it first. Do this by navigating to the install dir and typing "make clean" then "make uninstall" and then delete all remaining source files. To install XorHack copy the all files and folders that came with this readme onto your PS3 harddrive and then navigate to the location you copied them to.
Type "make" to build all parts of XorHack. Type "make install" to install all parts of XorHack. Type "make uninstall" to uninstall all parts of XorHack.
Running[edit | edit source]
- Once installed you can start the exploit loop from the command line by typing "ps3exploit 100" to perform the exploit loop 100 times.
- Once the exploit is successful the hypervisor can be dumped by typing "dumphv". It will dump it to a file in the current dir.
- Once the exploit is successful the bootloader can be dumped by typing "dumpbl". It will dump it to a file in the current dir.
GameOS dumper tools[edit | edit source]
Memdump[edit | edit source]
PS3 memory dumping tool that can dump lv1, lv2, NAND/NOR Flash, and eEID from GameOS.
Download[edit | edit source]
Applicable firmwares[edit | edit source]
| FW | lv1 | lv2 | Flash | eEID | 0.01 FINAL | |||
|---|---|---|---|---|---|---|---|---|
| Logs | Notes | |||||||
| <=2.60 CEX DEX | N / A | N / A | N / A | N / A | Not available as target version atm | |||
| 2.70 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 2.76 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 2.80 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.00 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.01 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.10 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.15 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.20 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.21 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.30 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.40 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.41 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.42 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.50 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.55 CEX DEX | Yes | Yes | Yes | Yes | ||||
| 3.56 CEX DEX | Pending | Pending | Pending | Pending | ||||
| =>3.60 CEX DEX | N / A | N / A | N / A | N / A | Not available as target version atm | |||
Legenda[edit | edit source]
- NA : Not Available as target version (mostly because of missing lv1:mmap114 or lv2:peek/poke patches)
- Yes: Fully supported
- No: Not supported
- Partial: Some functions work, others might not be complete
- Pending: No reports yet (help out by sending in your logs and dumps in a ZIP/RAR/7z!)
Known bugs[edit | edit source]
- buttons do not come back up after pressing -> to be fixed in v0.02 (button handler thread)
- exit app gives rightscreen black triangle -> to be fixed in v0.02 (cleanup RSX buffer)
- when free space is 0 bytes when dumping, application will halt -> to be fixed in v0.02 (check freespace first)
Current limitations[edit | edit source]
- Needs mmap114+peek/poke as minimal patches
- Can be buggy with strange spoofs
- No reports yet on Kiosk/SEX & Tool/DECR models
- NAND only : second bootldr at 0xF000000 - 0xF03FFFF (The last 256KB of flash) will be missing. Just copypaste the first bootldr 0x0000000 - 0x003FFFF (The first 256KB of flash), they are the same. Also, a console boots fine with only the first one.
flash dumper[edit | edit source]
precompiled:
- NOR flash - dump will take about 30 minutes, size: 16 MB (1 file: flash.bin)
- NAND flash - dumps will take more then 2½ hours, size: 239MB (1 file: flash.bin) with bootldr missing.
- NOR flash - The tool dumps the first 2 sectors of "VFLASH partition table" located inside "virtual flash" region on HDD, dump size 0x3FF (0x30 header + 0x90 per region)
git source:
lv1 dumper[edit | edit source]
precompiled:
- dump_lv1.pkg (70.11 KB) (glevand)
- lv1 dump will take about 30minutes, size: 16 MB (1 file: lv1.bin)
git source:
alternative:
- lv1dumper FLU1_T_2011.zip (9.72 KB) (flukes1)
- This is an application which runs on the PS3 that you can compile and package using PSL1GHT and geohot’s tools. After running it, lv1 will be mapped at 0×8000000014000000 with read/write access, and you will be able to poke lv2 without the system shutting down.
lv2 dumper[edit | edit source]
precompiled:
- dump_lv2.pkg (70.11 KB) (glevand)
- lv2 dump will take considerable less than lv1dump, size: 8.5 MB (2 files: lv2.bin.0 & lv2.bin.1)
- lv2dump_07a.pkg (1.48 MB) (other)
- lv2 dump saves to harddrive, you'll have to ftp it out. no sourcecode available.
git source:
sysrom dumper[edit | edit source]
precompiled:
dump_sysrom.pkg (69.67 KB) (glevand)
- sysrom dump takes only few seconds, size: 256KB (1 file: sysrom.bin)
git source:
metldrdumper[edit | edit source]
precompiled:
dump_metldr.pkg (69.67 KB) (CMX / original source code by: Flatz)
- metldr dump takes only few seconds, size: 256KB (1 file: dump.bin)
source code:
vflash dumper[edit | edit source]
git source:
vsh dumper[edit | edit source]
precompiled:
pupx dev_flash[edit | edit source]
Extracts dev_flash files from ps3 updates. To extract them you just have to put PS3UPDAT.PUP in the same folder and launch it.
- http://hsreina.shadosoft-tm.com
- http://psx-scene.com/forums/f149/extract-dev_flash-ps3-update-74664/
- http://www.multiup.org/download/4884407dbbdc793549561d0d735ba8b1/pupx_dev_flash.rar
dev_flash and dev_flash3 unpacker[edit | edit source]
it's a simple dev_flash extractor for 3.56+ PUPs
Before using it: Change this line "TOOLS=/home/wargio/.ps3tools" with the path of your tools, example: TOOLS=/home/god/ps3dev/ps3tools
LINUX version: http://pastebin.com/kLrPFb7y
OSX version: http://pastebin.com/FDMbgyVk
Usage: unpack_dev_flash.sh <*.pup>
example: unpack_dev_flash.sh PS3UPDAT.PUP
core os extractor[edit | edit source]
it's a simple core os extractor for 3.56+ PUPs
Before using it: Change this line "TOOLS=/home/wargio/.ps3tools" with the path of your tools, example: TOOLS=/home/god/ps3dev/ps3tools
Linux/OSX: http://pastebin.com/1AkEgW3y
Usage: ./extract_coreos.sh <PUP>
example: extract_coreos.sh PS3UPDAT.PUP
Syscon FW Reader[edit | edit source]
This simple program will read and show information about a Syscon Firmware package.
To compile it, just run make.
SRC
SFO Reader[edit | edit source]
it will show useful informations, built initially for vita pkgs
To build it, just run make.
SRC -> Gitorious
Example of output:
[SFO HDR] 0x46535000 [SFO Version] 0x00000101 [SFO N] 13 Value(s) [SFO Values] 0x000000e4 [SFO Params] 0x0000016c [ SFO ] [ 1 ] APP_VER | Param: 01.00 [ 2 ] ATTRIBUTE | Param: 0x0 [ 3 ] BOOTABLE | Param: 0x1 [ 4 ] CATEGORY | Param: AV [ 5 ] LICENSE | Param: Library programs ©Sony Computer Entertainment Inc. Licensed for play on the PLAYSTATION®3 Computer Entertainment System or authorized PLAYSTATION®3 format systems. For full terms and conditions see the user's manual. This product is authorized and produced under license from Sony Computer Entertainment Inc. Use is subject to the copyright laws and the terms and conditions of the user's license. [ 6 ] PARENTAL_LEVEL | Param: 0x1 [ 7 ] PS3_SYSTEM_VER | Param: 03.4200 [ 8 ] REGION_DENY | Param: 0xfffffffd [ 9 ] RESOLUTION | Param: 0x1d [ 10 ] SOUND_FORMAT | Param: 0x307 [ 11 ] TITLE | Param: Netflix Instant Streaming [ 12 ] TITLE_ID | Param: NPUP00030 [ 13 ] VERSION | Param: 01.03
SFO2SFX[edit | edit source]
it's a really simple Sfo to sfx converter.
for now it's not able to convert from sfx to sfo (when i will have more time, i will write a SFX2SFO. deroad)
Download ps3tool_with_sfo2sfx (this is my full SRC. all the tools are already compiled)
Mirror
From
[SFO HDR] 0x00505346 [SFO Version] 0x00000101 [SFO N] 6 Value(s) [SFO Params Offsets] 0x000000b4 [ SFO ] [ 1 ] CATEGORY | Param: 2D [ 2 ] PARENTAL_LEVEL | Param: 0x1 [ 3 ] PS3_SYSTEM_VER | Param: 01.3100 [ 4 ] TITLE | Param: PS2 System Data [ 5 ] TITLE_ID | Param: NPIA00001 [ 6 ] VERSION | Param: 01.00
to
<?xml version="1" encoding="utf-8" standalone=yes"?> <paramsfo add_hidden="false"> <param key="CATEGORY" fmt="utf8" max_len="4">2D</param> <param key="PARENTAL_LEVEL" fmt="int32" max_len="4">1</param> <param key="PS3_SYSTEM_VER" fmt="utf8" max_len="8">01.3100</param> <param key="TITLE" fmt="utf8" max_len="128">PS2 System Data</param> <param key="TITLE_ID" fmt="utf8" max_len="16">NPIA00001</param> <param key="VERSION" fmt="utf8" max_len="8">01.00</param> </paramsfo>
make_his[edit | edit source]
Generates a PARAM.HIS file from a Unix-formatted text file https://github.com/jjolano/make_his
HIP2HIS[edit | edit source]
This app simply convert a PARAM.HIP file to PARAM.HIS http://www.mediafire.com/?rv6jajz3nfy53iw
ReactPSN .rap to .rif converter[edit | edit source]
This tool will convert .rap files to .rif. Place it to the ps3tools directory along with other tools and then place your idps and act.dat files to appropriate folders.
- usage: rap2rif <rap file> <rif file>
ReactPSN .rif -> .rap converter[edit | edit source]
Your concole's IDPS named idps is in the exdata file folder.
Your act.dat is also in the exdata file folder.
The usage:
rif2rap <xxx.rif> <xxx.rap>
or
rif2rap <xxx.rif>
http://www.mirrorcreator.com/files/SGL6EZCS/rif2rap.rar_links
.rifkey to ReactPSN .rap converter[edit | edit source]
This tool can convert rifkey (klicensee) file to .rap file.
rifkey2rap <rifkey file> <rap file>
ReactPSN .rap to .rifkey converter[edit | edit source]
This tool can convert .rap file to rifkey (klicensee) file.
rap2rifkey <rap file> <rifkey file>
Metldr extractor[edit | edit source]
Extract metldr of NOR/NAND dump.
usage: extract_metldr <flash.bin> <destination>
(or just use Flowrebuilder and extract all binary)
decompile/disassembly .NET[edit | edit source]
- http://ilspy.net/
- http://www.devextras.com/decompiler/
- http://www.jetbrains.com/decompiler/
- http://www.telerik.com/products/decompiler.aspx
- http://www.reflector.net/
Total Commander[edit | edit source]
- Handy for searching static values (such as sboxes or curves) recursively in folders
- Also useful to know where keys exist (in which elf they are located)
- http://www.ghisler.com/
PkgView[edit | edit source]
- By ifcaro, web, source code
SPRXPatcher[edit | edit source]
- A modern PlayStation 3 ELF patcher to load SPRX files
- Source code