SLB2: Difference between revisions
Jump to navigation
Jump to search
Red-EyeX32 (talk | contribs) mNo edit summary |
No edit summary |
||
| Line 46: | Line 46: | ||
You are able to decrypt inner pup files using the follow keys: | You are able to decrypt inner pup files using the follow keys: | ||
erk=DB7A24EC38BDB45B98CCD7D363EA2AF0C326E65081E0630CB9AB2D215865878A | |||
riv=C9205F46F6021697E670F13DFA726212 | |||
pub=A8FD6DB24532D094EFA08BD35C9A72287D905C6B27B42BE4AB925AAF4AFFF34D41EEB54DD128700D | |||
priv=001AD976FCDE86F5B8F63453EF3A7F94E861975BA3 | |||
ctype=30 | |||
0x40 bytes after the magic are encrypted with aes. (256 bits CBC Mode). The new encrypted buffer contains the new erk and riv to be used for the next decryption. The next 0x240 bytes are decrypted with aes. (128 bits CTR Mode). That 0x240 bytes contain a table of information relating to the system files. Each entry in there contains the offset for encrypted sections, sha1 hmac keys, and the erk and riv to decrypt each encrypted section. Each section is decrypted using aes. (128 bits CTR mode). | |||
{{Software}} | {{Software}} | ||
<noinclude>[[Category:Main]]</noinclude> | <noinclude>[[Category:Main]]</noinclude> | ||
Revision as of 09:47, 23 March 2014
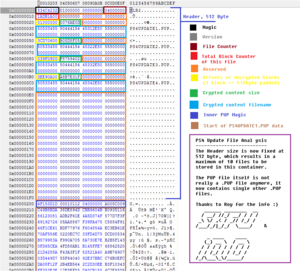
SLB2 structure
/* file structure of SLB goes as following, if unpacking make sure you use 64 bits little endian on windows os */
typedef unsigned char u8;
typedef unsigned long int u32;
typedef unsigned long long int u64;
typedef struct{
u32 offset; //1 block is headersize (512 padded)
u32 cryptSize;
u64 reserved; //probably file alignment
u8 fileName[32];
} fileEntry;
typedef struct{
u32 magic; //SLB2
u64 version; //1
u32 fileCount;
u32 blockCount;
u8 reserved[12];
fileEntry files[10];
} ps4pup;
SLB2 files to play with
* https://mega.co.nz/#!WE8zUAyb!ZuZy5Vxrd4eCc4bTvFW_ZC7lu7Ub0tcdyE08xbJtrok (Main)
- http://dus01.ps4.update.playstation.net/update/ps4/image/2013_1112/sys_df008b5601f4a214a3cc65030a02ac4a/PS4UPDATE.PUP?dest=us (Main)
- http://dus01.ps4.update.playstation.net/update/ps4/image/2013_1112/rec_cedada625478db608d5878c019454380/PS4UPDATE.PUP?dest=us (Recovery)
Unpacking
- http://pastie.org/private/4wgojewhp2pq7declhkhw (flatz)
- PS4 PUP Extractor v2 (xerpi)
- PS4 FW Tool v1.0.0 (skfu)
- https://github.com/Hykem/ps4tools (hykem, based on flatz)
- https://github.com/Jakes625/PS4-PUP-Tool (Jakes625)
SLB PUP Files
These files are contained inside of SLB2 containers. They contain data pertaining to system firmware.
You are able to decrypt inner pup files using the follow keys:
erk=DB7A24EC38BDB45B98CCD7D363EA2AF0C326E65081E0630CB9AB2D215865878A riv=C9205F46F6021697E670F13DFA726212 pub=A8FD6DB24532D094EFA08BD35C9A72287D905C6B27B42BE4AB925AAF4AFFF34D41EEB54DD128700D priv=001AD976FCDE86F5B8F63453EF3A7F94E861975BA3 ctype=30
0x40 bytes after the magic are encrypted with aes. (256 bits CBC Mode). The new encrypted buffer contains the new erk and riv to be used for the next decryption. The next 0x240 bytes are decrypted with aes. (128 bits CTR Mode). That 0x240 bytes contain a table of information relating to the system files. Each entry in there contains the offset for encrypted sections, sha1 hmac keys, and the erk and riv to decrypt each encrypted section. Each section is decrypted using aes. (128 bits CTR mode).