Talk:Playstation Update Package (PUP): Difference between revisions
m (moved to Recovery_Menu) |
m (moved to Cinavia_(DRM)) |
||
| Line 249: | Line 249: | ||
Note: console needs to run at least FW 2.50? (2.30 didn't work) | Note: console needs to run at least FW 2.50? (2.30 didn't work) | ||
---- | ---- | ||
Revision as of 17:58, 12 March 2013
Playstation Update Package (PUP) - Discussion/Talk
What is the part that defines, what firmware it really is?. I mean, for firmwares below 3.55 we have all the keys so whe can forge any PUP and make it appear as a +3.55, that would be a way to downgrade, without the need of a dongle and recovery mode.
I know there are version strings in pupheader,version.txt, info0, and in vsh.self.. but what is missing? What isn´t correclty set in mfw to make it pass the checks of a legit +3.55 fw?
We are using recovery mode to downgrade because, we haven´t found a way to create a legit +3.55
Unpacking a firmware
Unpack the PUP
Dots.txt EULA.xml Update_Files.tar Updater.self Version.txt VSH.tar Zeros.bin
Untar the Update_Files.tar
BDIT_FIRMWARE_PACKAGE.pkg BDPT_FIRMWARE_PACKAGE_301R.pkg BDPT_FIRMWARE_PACKAGE_302R.pkg BDPT_FIRMWARE_PACKAGE_303R.pkg BDPT_FIRMWARE_PACKAGE_304R.pkg BDPT_FIRMWARE_PACKAGE_306R.pkg BDPT_FIRMWARE_PACKAGE_308R.pkg BLUETOOTH_FIRMWARE.pkg CORE_OS_PACKAGE.pkg dev_flash3_022.tar.aa.2010_11_27_051800 dev_flash_000.tar.aa.2010_11_27_051337 dev_flash_001.tar.aa.2010_11_27_051337 dev_flash_002.tar.aa.2010_11_27_051337 dev_flash_003.tar.aa.2010_11_27_051337 dev_flash_004.tar.aa.2010_11_27_051337 dev_flash_005.tar.aa.2010_11_27_051337 dev_flash_006.tar.aa.2010_11_27_051337 dev_flash_007.tar.aa.2010_11_27_051337 dev_flash_008.tar.aa.2010_11_27_051337 dev_flash_009.tar.aa.2010_11_27_051337 dev_flash_010.tar.aa.2010_11_27_051337 dev_flash_011.tar.aa.2010_11_27_051337 dev_flash_012.tar.aa.2010_11_27_051337 dev_flash_013.tar.aa.2010_11_27_051337 dev_flash_014.tar.aa.2010_11_27_051337 dev_flash_015.tar.aa.2010_11_27_051337 dev_flash_016.tar.aa.2010_11_27_051337 dev_flash_017.tar.aa.2010_11_27_051337 dev_flash_018.tar.aa.2010_11_27_051337 dev_flash_019.tar.aa.2010_11_27_051337 dev_flash_020.tar.aa.2010_11_27_051337 dev_flash_021.tar.aa.2010_11_27_051337 MULTI_CARD_FIRMWARE.pkg RL_FOR_PACKAGE.img RL_FOR_PROGRAM.img SYS_CON_FIRMWARE_01000006.pkg SYS_CON_FIRMWARE_01010303.pkg SYS_CON_FIRMWARE_01020302.pkg SYS_CON_FIRMWARE_01030302.pkg SYS_CON_FIRMWARE_01040402.pkg SYS_CON_FIRMWARE_01050002.pkg SYS_CON_FIRMWARE_01050101.pkg SYS_CON_FIRMWARE_S1_00010002083E0832.pkg UPL.xml.pkg
unpkg CORE_OS_PACKAGE.pkg
content info0 info1
cosunpkg content from CORE_OS_PACKAGE.pkg
aim_spu_module.self appldr creserved_0 default.spp emer_init.self eurus_fw.bin hdd_copy.self isoldr lv0 lv1.self lv1ldr lv2ldr lv2_kernel.self manu_info_spu_module.self mc_iso_spu_module.self me_iso_spu_module.self sb_iso_spu_module.self sc_iso.self sdk_version spp_verifier.self spu_pkg_rvk_verifier.self spu_token_processor.self spu_utoken_processor.self sv_iso_spu_module.self
unself the self's
...
unpkg dev_flash*
content info0 info1
untar dev_flash* content
...
3.55 example
PSUPDATE.PUP ├── dots.txt ├── license.txt ├── ps3swu.self ├── update_files.tar │ ├── BDIT_FIRMWARE_PACKAGE.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_301R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_302R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_303R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_304R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_306R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BDPT_FIRMWARE_PACKAGE_308R.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── BLUETOOTH_FIRMWARE.pkg │ │ ├── content │ │ │ ├── RC29_firmware_footer.dfu │ │ │ ├── usb8780-5.0.1-A1-A2.dfu │ │ │ └── usb8781-20.0.12.0.dfu │ │ ├── info0 │ │ └── info1 │ ├── CORE_OS_PACKAGE.pkg │ │ ├── aim_spu_module.self │ │ ├── appldr │ │ ├── creserved_0 │ │ ├── default.spp │ │ ├── emer_init.self │ │ ├── eurus_fw.bin │ │ ├── hdd_copy.self │ │ ├── isoldr │ │ ├── lv0 │ │ ├── lv1ldr │ │ ├── lv1.self │ │ ├── lv2_kernel.self │ │ ├── lv2ldr │ │ ├── manu_info_spu_module.self │ │ ├── mc_iso_spu_module.self │ │ ├── me_iso_spu_module.self │ │ ├── sb_iso_spu_module.self │ │ ├── sc_iso.self │ │ ├── sdk_version │ │ ├── spp_verifier.self │ │ ├── spu_pkg_rvk_verifier.self │ │ ├── spu_token_processor.self │ │ ├── spu_utoken_processor.self │ │ └── sv_iso_spu_module.self │ ├── dev_flash_XXX.tar.aa.DATE/TIME │ ├── dev_flash3_XXX.tar.aa.DATE/TIME │ ├── MULTI_CARD_FIRMWARE.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── RL_FOR_PACKAGE.img │ ├── RL_FOR_PROGRAM.img │ ├── SYS_CON_FIRMWARE_01000006.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01010303.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01020302 │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01030302.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01040402.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01050002.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_01050101.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ ├── SYS_CON_FIRMWARE_S1_00010002083E0832.pkg │ │ ├── content │ │ ├── info0 │ │ └── info1 │ └── UPL.xml.pkg │ ├── content │ ├── info0 │ └── info1 ├── update_files.tar ├── update_flags.txt ├── version.txt └── vsh.tar
Adding new keys to older firmwares
patch the loaders add keys to appldr keys index & tables there are also npdrm keys inside appldr as well, add the 3.56++ ones appldr,. lv2.self and game_ext_plugin need patching for new games support vsh.self maybe too
Creating a MFW? (3.41/3.55 with 3.56 keys)
Proof of concept with added keys to appldr (and none of the other mentioned files above) : http://www.ps3devwiki.com/wiki/Talk:Patches#appldr_3.55_add_3.56.2F3.60_keys
Using fake upgrade to get lowest firmware version info
http://ps3devwiki.com/files/firmware/MFW-CEX/MinVerCheck/ // MinVerChk.rar (1.28 KB) / mirror
CRC-16: 9A11 CRC-32 (Ethernet and PKZIP): 50EE9A92 SHA-1: 1B60E0ADE8E698D9796AA78B7AD54B10E05A9B0B MD-5: BB39828156BC7DF144E4D06D81C801AB
- Unrar and copy this MinVerChk PUP to your USB stick (/PS3/UPDATE/PS3UPDAT.PUP), the same way as if it was an firmware upgrade.
- Insert the USB stick into the PS3.
- Start a firmware update like normal from XMB (Don’t worry, it will not update!)
- It will shortly fail and display the Firmware Base Value
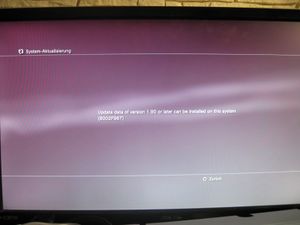
Note: console needs to run at least FW 2.50? (2.30 didn't work)
Hashes
| Version | MD5 | SHA1 | CRC32 | CRC16 | HMAC_SHA1 |
|---|---|---|---|---|---|
| 0 file (do not use) | MD5::1f5039e50bd66b290c56684d8550c6c2 | SHA1::7b91dbdc56c5781edf6c8847b4aa6965566c5c75 | CRC32::2A0E7DBB | CRC16::0 | HMAC_SHA1:: |
| 3.41 RETAIL/CEX PSJB | MD5::6f1ef9144c43c9a6f00f7ee7464a6689 | SHA1::f3c19e06c0e7b8cc550bb3244f5f88356173fa6d | CRC32::8A1E7548 | CRC16::7FFC | HMAC_SHA1::9F7001A6A93AE03A61ED7CFB7156A68DF0740708 |
Repositories
stoker25 - specialises in debug/DEX and DECR/TOOL firmwares (self hosted)
Remark @ Installation
ps3d storage region 3 on the internal harddisk (ps3dc) is used by the PS3 as temp for installing updates. When installing PUP files, the PUP content gets unpacked there, checked - the system flags the update bit and prompts for reboot. After reboot it sees the update bit set and installs the files from ps3dc without rechecking (!) -> possible attack vector for circumventing checks, like down-/crossgrading). edit-note: doesn't seem to be true, it is still checked.
ps3d - 4 possible regions :
ps3da : whole disk ps3db : UFS2 : GameOS ps3dc : FAT (2GB) : Update ps3dd : EXT3 : OtherOS (in the <=3.15 way)
Factory Service Mode - Installation log breakdown
Explaination from rms: http://rmscrypt.wordpress.com/2011/02/01/the-downgrade-process/
Sample logs:
- http://pastebin.com/XhcjfAjw (downgrade 3.66 -> 3.15)
- http://pastebin.com/SAN7Z3Dq (UPL 3.15)
| log | Explaination | Notes |
|---|---|---|
| manufacturing bit detection in Syscon eeprom, manufacturing mode enabled, looking for lv2_diag.self | ||
manufacturing updating start |
lv2_diag.self initialised | |
PackageName = /dev_usb000/PS3UPDAT.PUP |
PUP file used for FSM reinstall on USB root | |
settle polling interval success |
||
vflash is disabled... boot from nand flash... |
NAND system detected, vflash disabled | |
creating flash regions... create storage region: (region id = 2) format partition: (region_id = 2, CELL_FS_IOS:BUILTIN_FLSH1, CELL_FS_FAT) create storage region: (region id = 3) format partition: (region_id = 3, CELL_FS_IOS:BUILTIN_FLSH2, CELL_FS_FAT) create storage region: (region id = 4) format partition: (region_id = 4, CELL_FS_IOS:BUILTIN_FLSH3, CELL_FS_FAT) create storage region: (region id = 5) create storage region: (region id = 6) |
creating and formatting FLASH regions 2, 3, 4, 5, 6 | |
Initializing taking a while... start Updating Proccess Initialize elapsed time = 61 msec |
Initializing + Start Updating Proccess | |
check UPL Check UPL elapsed time = 34 msec check Package Size get package size elapsed time = 8 msec start Updating Package Update packages num = 29 Update packages total size = 160699026 |
UPL.xml.pkg from PUP unpkg'ed and read | |
Update Package Revoke list read package revoke list package (576 bytes) elapsed = 6 msec update package revoke list elapsed = 331 msec Update Package Revoke list done(0x8002f000) |
RL_FOR_PACKAGE.img copied from PUP to trvk_pkg | |
Update Core OS Package read core os package (5193774 bytes) elapsed = 324 msec update core os package elapsed = 1965 msec Update Core OS Package done(0x8002f000) |
Core OS package (CORE_OS_PACKAGE.pkg) is unpkg'ed from PUP and written to ros | |
Update VSH Package sys_memory_container_create() success(id = 0xc0effffe) Update VSH's package : 1/21 read vsh package (2070 bytes) elapsed = 8 msec decrypt and verify vsh package elapsed = 23 msec write vsh package elapsed = 9259 msec compare vsh package elapsed = 0 msec Update VSH's package : 2/21 read vsh package (5616383 bytes) elapsed = 351 msec decrypt and verify vsh package elapsed = 341 msec write vsh package elapsed = 1725 msec compare vsh package elapsed = 402 msec Update VSH's package : 3/21 read vsh package (3357780 bytes) elapsed = 214 msec decrypt and verify vsh package elapsed = 227 msec write vsh package elapsed = 2926 msec compare vsh package elapsed = 312 msec Update VSH's package : 4/21 read vsh package (5240122 bytes) elapsed = 328 msec decrypt and verify vsh package elapsed = 309 msec write vsh package elapsed = 2776 msec compare vsh package elapsed = 399 msec Update VSH's package : 5/21 read vsh package (24029 bytes) elapsed = 9 msec decrypt and verify vsh package elapsed = 24 msec write vsh package elapsed = 1185 msec compare vsh package elapsed = 9 msec Update VSH's package : 6/21 read vsh package (9831317 bytes) elapsed = 599 msec decrypt and verify vsh package elapsed = 279 msec write vsh package elapsed = 11830 msec compare vsh package elapsed = 466 msec Update VSH's package : 7/21 read vsh package (8662380 bytes) elapsed = 539 msec decrypt and verify vsh package elapsed = 272 msec write vsh package elapsed = 16532 msec compare vsh package elapsed = 474 msec Update VSH's package : 8/21 read vsh package (8657372 bytes) elapsed = 541 msec decrypt and verify vsh package elapsed = 361 msec write vsh package elapsed = 5911 msec compare vsh package elapsed = 448 msec Update VSH's package : 9/21 read vsh package (10445426 bytes) elapsed = 635 msec decrypt and verify vsh package elapsed = 255 msec write vsh package elapsed = 5408 msec compare vsh package elapsed = 467 msec Update VSH's package : 10/21 read vsh package (10252830 bytes) elapsed = 641 msec decrypt and verify vsh package elapsed = 262 msec write vsh package elapsed = 8646 msec compare vsh package elapsed = 476 msec Update VSH's package : 11/21 read vsh package (9922968 bytes) elapsed = 621 msec decrypt and verify vsh package elapsed = 252 msec write vsh package elapsed = 6950 msec compare vsh package elapsed = 467 msec Update VSH's package : 12/21 read vsh package (8214459 bytes) elapsed = 505 msec decrypt and verify vsh package elapsed = 199 msec write vsh package elapsed = 5843 msec compare vsh package elapsed = 386 msec Update VSH's package : 13/21 read vsh package (9428094 bytes) elapsed = 594 msec decrypt and verify vsh package elapsed = 244 msec write vsh package elapsed = 5238 msec compare vsh package elapsed = 442 msec Update VSH's package : 14/21 read vsh package (7973335 bytes) elapsed = 498 msec decrypt and verify vsh package elapsed = 346 msec write vsh package elapsed = 13617 msec compare vsh package elapsed = 456 msec Update VSH's package : 15/21 read vsh package (9766737 bytes) elapsed = 603 msec decrypt and verify vsh package elapsed = 360 msec write vsh package elapsed = 17267 msec compare vsh package elapsed = 529 msec Update VSH's package : 16/21 read vsh package (9199234 bytes) elapsed = 583 msec decrypt and verify vsh package elapsed = 407 msec write vsh package elapsed = 23189 msec compare vsh package elapsed = 689 msec Update VSH's package : 17/21 read vsh package (7260896 bytes) elapsed = 466 msec decrypt and verify vsh package elapsed = 286 msec write vsh package elapsed = 14751 msec compare vsh package elapsed = 689 msec Update VSH's package : 18/21 read vsh package (6563380 bytes) elapsed = 422 msec decrypt and verify vsh package elapsed = 155 msec write vsh package elapsed = 1906 msec compare vsh package elapsed = 357 msec Update VSH's package : 19/21 read vsh package (6092245 bytes) elapsed = 373 msec decrypt and verify vsh package elapsed = 227 msec write vsh package elapsed = 1457 msec compare vsh package elapsed = 405 msec Update VSH's package : 20/21 read vsh package (9859067 bytes) elapsed = 590 msec decrypt and verify vsh package elapsed = 238 msec write vsh package elapsed = 2187 msec compare vsh package elapsed = 498 msec Update VSH's package : 21/21 read vsh package (6492084 bytes) elapsed = 419 msec decrypt and verify vsh package elapsed = 321 msec write vsh package elapsed = 17509 msec compare vsh package elapsed = 674 msec Update VSH Package done(0x8002f000) |
dev_flash_000.tar.aa.* files from PUP are unpkg'ed to dev_flash | |
Bul-ray Disc Player Revoke read bdp revoke package (1904 bytes) elapsed = 23 msec decrypt and verify bdp revoke package elapsed = 29 msec write bdp revoke package elapsed = 2240 msec compare bdprevoke package elapsed = 57 msec Bul-ray Disc Player Revoke done(0x8002f000) |
dev_flash3_024.tar.aa.* files from PUP are unpkg'ed to dev_flash3 | |
Update Program Revoke list read program revoke list package (704 bytes) elapsed = 7 msec update program revoke list elapsed = 331 msec Update Program Revoke list done(0x8002f000) |
RL_FOR_PROGRAM.img from PUP is copied to trvk_prg | |
move_2block_status_into_the_region(): region id = 3 rewrite_region() region id = 0x3, start_lba = 0x0, end_lba = 0x4000 rewrite region done (ret = 0x8002f000) rewrite region elapsed time = 1262 msec touch_1st_sector_in_block() region id = 0x3, start_lba = 0x0, end_lba = 0x4000 touch_1st_sector() done (ret = 0x8002f000) touch_1st_sector() elapsed time = 1121 msec rewrite_region() region id = 0x3, start_lba = 0x0, end_lba = 0x4000 rewrite region done (ret = 0x8002f000) rewrite region elapsed time = 1262 msec |
||
Update BD firmware read BD firmware package (1966992 bytes) elapsed = 142 msec update BD firmware elapsed = 184 msec read BD firmware package (951040 bytes) elapsed = 78 msec update BD firmware elapsed = 142 msec read BD firmware package (951040 bytes) elapsed = 80 msec update BD firmware elapsed = 13959 msec Update BD firmware done(0x8002f000) |
Appropiate BD firmware for that Bluray Drive is flashed to BD eeprom | |
Update Multi-Card controller firmware read MCC package (28636 bytes) elapsed = 25 msec update MCC elapsed = 24 msec Update Multi-Card controller firmware done(0x8002f000) |
If SKU with MultiCardReader then Multi-Card controller firmware is flashed to SST 1mbit Flash | |
Update BlueTooth firmware read BT package (639368 bytes) elapsed = 62 msec update BT elapsed = 56 msec Update BlueTooth firmware done(0x8002f000) |
Bluetooth NOR flash is updated with | |
Update System controller firmware read SC patch package (4864 bytes) elapsed = 24 msec read SC patch package (4864 bytes) elapsed = 24 msec read SC patch package (4864 bytes) elapsed = 23 msec Update System controller firmware done(0x8002f000) |
Syscon Hardware is updated with appropiate System controller firmware | |
update package elapsed time = 228361 msec |
||
post processiong... post processiong done cleanup update status (ret = 0) |
||
os version = 03.1500 build_version = 38031,20091206 |
||
region of core os package = 0x40000000 |
||
build_target = CEX-ww build target id = 0x83 |
||
manufacturing updating SUCCESS(0x8002f000) |
||
set product mode (ret = 0) |
||
Total Elapsed time = 230556 msec |
old crossgrading Retail/CEX to Debug/DEX
Note
For this to work your system must be below or at 1.80 for the 1.80 debug update and below or on 2.01 for the 2.15 debug update. Just use the next version up from your current firmware version for the retail update.
It's not very usefull, esp. nowadays, added for historic reasons
How to install debug firmware on retail PS3
Tools needed
- 1 PS3 system
- 2 PS3 hard drives that are the same size
- 1 retail firmware upgrade
- 1.80 Or 2.15 debug firmware
Instructions
- Format both hard drives on the PS3 system.
- Download a debug PS3 firmware and place it in USB stick, and start the update. This will copy all the debug firmware files to the PS3's HDD-A.
- After copied the PS3 will restart and you will see the normal update menu which prompts you to click the button to start update. Do NOT update your PS3, but power it off.
- Next remove the HDD-A, and place in the second HDD, HDD-B in the PS3.
- Download and copy a retail PS3 firmware to a USB stick.
- Again as before place USB in PS3 and update the PS3 as normal but when you get to the screen where it asks for you to press button, do that but stop when it asks you to AGREE to Terms and Condition Page.
- While the system is still powered on and on the update screen, REMOVE HDD-B, and insert HDD-A.
- After swapping the HDD's continuie to update the PS3 as normal and the PS3 will install the debug PS3 firmware=
- Go to the settings and check firmware version and there you will also see the debugging PS3 options :)
Ancient preproduction / prototype
CEB-201x, DEH-R1030 etc. old SDKs contain these binairy files in \cell\target\bootrom, while knowledge about previous version existance can be revealed by the documentation in \cell\info\old\XXX
ebootrom structure
Header
| Offset | Length | Type | Information |
|---|---|---|---|
| 0x0 | 0x4 | unsigned long | Unknown |
| 0x4 | 0x4 | unsigned long | File Count |
| 0x8 | 0x8 | unsigned long | File Length |
| 0x10 | 0x30 * File Count | File Table | File Table |
File Table
The file table consists of a number of file entries determined by File Count, with the format below:
| Offset | Length | Type | Information |
|---|---|---|---|
| 0x0 | 0x8 | unsigned long | Data Offset |
| 0x10 | 0x8 | unsigned long | Data Length |
| 0x20 | 0x20 | unsigned long | Data FileName (see below) |
Filename IDs
| File Entry ID | Filename |
|---|---|
| 0x1 | sdk_version |
| 0x2 | version.txt |
| 0x3 | ros (CORE_OS_PACKAGE.pkg) |
| 0x4 | trvk_prg |
| 0x5 | trvk_pkg |
| 0x6 | nand_update |
| 0x7 | bdit_firmware |
| 0x8 | bdpt_301r_firmware |
| 0x9 | bdpt_303r_firmware |
bdit_firmware / bdpt_301r_firmware / bdpt_303r_firmware / nand_update / ros / trvk_pkg / trvk_prg
Header
| Offset | Length | Type | Information |
|---|---|---|---|
| 0x0 | 0x4 | unsigned long | Unknown |
| 0x4 | 0x4 | unsigned long | File Count |
| 0x8 | 0x8 | unsigned long | File Length |
| 0x10 | 0x30 * File Count | File Table | File Table |
File Table
The file table consists of a number of file entries determined by File Count, with the format below:
| Offset | Length | Type | Information |
|---|---|---|---|
| 0x0 | 0x8 | unsigned long | Data Offset |
| 0x10 | 0x8 | unsigned long | Data Length |
| 0x20 | 0x20 | unsigned long | DataName
|
| 0x40 | Data Length | unsigned long | SCE signed package data |
CORE_OS_PACKAGE.pkg
| File Entry ID | Filename |
|---|---|
| aim_spu_module.self | |
| appldr | |
| creserved_0 | |
| default.spp | |
| isoldr | |
| lv0 | |
| lv1.self | |
| lv1ldr | |
| lv2_kernel.self | |
| lv2ldr | |
| mc_iso_spu_module.self | |
| me_iso_spu_module.self | |
| rvkldr | |
| sb_iso_spu_module.self | |
| sc_iso.self | |
| sdk_version | |
| spp_verifier.self | |
| spu_pkg_rvk_verifier.self | |
| spu_token_processor.self | |
| sv_iso_spu_module.self | |
| sys_init_app.self | |
| sys_init_ios.self | |
| sysctl.txt |
known updates
0.2 ebootrom
0.3 ebootrom
0.60 ebootrom
0.60: lv0 contains string : 'Sony CXD9823 NAND Controller'
Boot Loader SE Version 0.6 2006-01-31_13:53:04
Boot Loader SE Version 0.5.2005-12-28_16:10:53
0.80 ebootrom
key: rev 0x00
0.84 ebootrom
0.84: lv0 doesnt contain previous mentioned string
from decrypted lv0 0.84: Boot Loader SE Version 0.8.4 (Build ID: 822,8517, Build Data: 2006-05-16_17:50:21)
0.85 ebootrom
0.90 ebootrom
0.90 PUP
? 0.90: PS3UPDAT.PUP format was implemented since 0.90 ?
0.92 ebootrom
key: rev 0x01 + NP rev 0x01
0.93 ebootrom
0.94 ebootrom
0.95 PUP
0.96 PUP
100.002 ebootrom
from decrypted lv0: Boot Loader SE Version 1.0.0 (Build ID: 1643,16413, Build Data: 2006-10-05_16:32:34)